A Guide to Effective Cybersecurity Risk Management - Bitdefender TechZone
This guide provides a structured framework for effective risk management. Learn how to identify, assess, and prioritize critical risks, implement robust mitigation strategies, and ensure business continuity. Discover how to demonstrate the value of your cybersecurity investments to stakeholders and achieve a strong security posture.
Imagine a mid-sized business that maybe believed it was too small to be targeted by cybercriminals. One day, its entire network is locked by ransomware, paralyzing operations for days and causing significant reputational damage, as well as a loss of revenue due to business disruptions. How could this have been avoided?
Understanding the value of your organization goes beyond just the value of your assets—it includes the internal relationships and dependencies on external partners, vendors, and third-party services. To build a strong risk management strategy, you must first understand the full scope of risks your organization faces.
This document will guide you through effective risk management, starting by identifying, calculating, and prioritizing risks. It shows how effective mitigation, incident response, enabled by Bitdefender solutions, and continuity strategies can safeguard your assets and stakeholders. You will learn how to demonstrate the value of cybersecurity in terms business leaders can relate to, ensuring it is seen as an investment rather than a cost.
Understanding Cyber Risk
Cyber risk is the combination of likelihood and impact of your organization experiencing data loss or operational damage due to security incidents. The severity of a cyber risk can vary depending on the size of your organization and its industry.
Larger organizations typically face more significant cyber risks due to the scale and complexity of their IT infrastructure, as well as the higher value of their data and operations. Smaller organizations may have fewer resources for cybersecurity, but they often operate under the incorrect assumption that they are less likely to be targeted—which can make them the initial point for supply chain attacks, putting their business partners at risk.
Cyber risks are typically categorized into five areas:
Strategic Risk: This refers to risks that can impact long-term goals such as brand position or business activity, especially those related to strategic alliances. For example, a company planning a strategic alliance to jointly develop a new product may face significant strategic risk. A cyberattack on either partner during the alliance formation phase could compromise confidential information shared during negotiations, such as intellectual property or customer data.
Operational Risk: This includes risks that often disrupt normal operations, like ransomware attacks.
Financial Risk: This includes direct costs like ransom payments or legal fees, as well as indirect costs like revenue loss.
Reputational Risk: A security incident could damage an organization's reputation and cause customers to lose trust, resulting in a decline in customer loyalty or market share.
Regulatory Risk: Many organizations must follow regulations, and failure to comply or experience a breach can result in fines like those imposed by the GDPR.
Risk Measurement
Cyber risk is often calculated using the formula:
Risk = Likelihood x Impact
where:
Likelihood is the probability of a vulnerability being exploited by a threat actor. It can be further broken down as:
Vulnerability – A weakness or misconfiguration in a system or process that could be exploited. By minimizing vulnerabilities (as discussed in the Risk Mitigation Strategies section), you can significantly reduce the likelihood of a successful attack.
Threat Actor – Refers to the attacker exploiting the vulnerability. Threat actors can include cybercriminals seeking financial gain, nation-states pursuing espionage or sabotage, hacktivists with political or ideological motives, or insiders (employees or contractors) with access to sensitive systems. Each type of threat actor has different motivations and methods, so the risk they pose varies depending on your organization's nature.
Impact - The potential damage or loss that could occur if the vulnerability is exploited. While the impact can be significant, it can be mitigated through various strategies. For example, implementing an Incident Response Plan (as discussed in the Incident Response and Business Continuity section) and ensuring stakeholders are informed and prepared can reduce the overall attack impact.
Identifying and Assessing Risks
The key step to effective cyber risk management is to identify and document all assets in an asset inventory. As an asset, you should consider:
Employees: Individuals who have access to your organizational systems or data.
IT (Information Technology): Servers, databases, workstations, software, and more.
IoT (Internet of Things): Smart devices, sensors, connected cameras, etc.
OT (Operational Technology): Industrial control systems, SCADA, critical infrastructure.
Cloud: Cloud environments, platforms, applications, data storage.
Third-Parties Risks:
Vendors, suppliers, service providers (e.g., SaaS providers, data processors).
Contractors, and other independent individuals (e.g., intern, volunteer) who have access to your organizational systems or data.
Note
Keep in mind that asset management is not a one-time process, it requires continuous review and updates to remain effective, which has to be built into every relevant process, from procurement, joiners, movers and leavers, and more. Automation should be leveraged wherever feasible to streamline these processes and enhance accuracy.
Once you have a clear inventory of all assets, the next step is to start identifying the risks. This includes pinpointing assets that store or process sensitive data, determining critical assets essential for operations, understanding how assets interact with each other, and establishing procedures for managing external, outdated, or unsupported assets.
To identify vulnerabilities in systems and networks such as unpatched systems you can review and monitor the NIST National Vulnerability Database, a repository of officially known security vulnerabilities. However, this requires manual verification to confirm that the specific software versions and configurations used within your organization are actually listed and referenced in the NIST database. Alternatively, automated tools like Bitdefender Risk Management and External Attack Surface Management (EASM) can streamline the process.
To identify vulnerabilities in applications, people, and processes, such as exploitable security gaps or inadequate incident response plans, you can conduct Penetration Testing or Red Teaming exercises. These methods simulate attacks and allow you to evaluate your security posture and processes from an attacker's perspective.
Risk Assessment
Risk assessment can involve various steps and matrices depending on the chosen methodology, or framework. In this document, for simplicity, we will focus on an approach where risk assessment involves considering the likelihood of a threat occurring and its potential impact. This can be represented in a simple matrix with four quadrants:
| 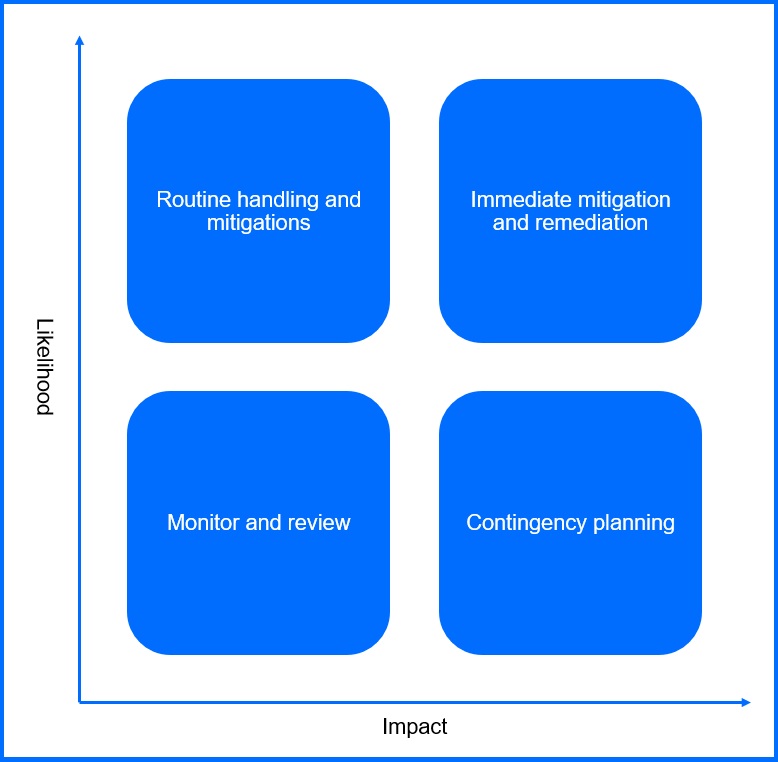 |
|
Let us consider how a supply chain attack depending on the different usage scenario can land into two different quadrants. In the first scenario, we can imagine a typical software supply chain attack where an attacker gained access to IT service management software. Through this compromised software, they could potentially compromise any company using this software. Such events are low likelihood but highly impactful. On the other hand, we have business email compromise (BEC) where threat actors attempt to manipulate employees into transferring funds or disclosing sensitive information. This kind of supply chain attack has a high likelihood and high impact.
It is often challenging to assess the risk accurately without understanding how different risks are interconnected. Imagine managing vulnerability solely based on the Common Vulnerability Scoring System (CVSS). If you are dealing with high-scored vulnerabilities, you might miss those with lower points that could lead to more critical consequences. For example, a vulnerability in a content management system (CMS) that allows for remote code execution (RCE) might have a CVSS of 9.8. The attacker may have initial access to a system but still need another vulnerability to escalate privileges and gain access to sensitive data or system control. In contrast, a vulnerability in a cryptographic library that allows for reading encrypted data might have a CVSS of 5.9 but can lead to significant data breaches.
Risk Management Framework
Risk Management Framework provides structured methodologies for identifying, assessing, and mitigating risks, enabling you to prioritize security initiatives and allocate resources effectively.
They facilitate better communication and decision-making regarding cybersecurity priorities. Key frameworks include:
NIST Risk Management Framework (RMF): This framework provides a structured process for integrating security, privacy, and risk management activities into the system development lifecycle.
ISO 27005: An international standard focusing on information security risk management, providing a framework for assessing, treating, and monitoring information security risks.
CIS Critical Security Controls (CISv8): This framework outlines a set of best practices for securing IT systems and data, focusing on critical actions to mitigate risks.
MITRE ATT&CK: A knowledge base of adversary tactics and techniques based on real-world observations, useful for threat modeling and defense strategies.
Implementing a framework helps structure your security programs by defining roles, establishing risk management processes, and developing incident response plans. Additionally, using frameworks allows you to benchmark your security posture against industry standards, promoting a holistic view that considers people, processes, and technology.
You should adopt a risk management framework that fits your needs. This involves:
Assessing Current Practices: Evaluate existing security measures and identify gaps.
Selecting a Framework: Choose a framework aligned with your organizational goals and compliance requirements, and that aligns with the Enterprise Risk Management (ERM) methodology.
Integration into Processes: Incorporate the framework into existing security and business processes for alignment and effectiveness.
Regular Reviews and Updates: Continuously review and update risk management practices to adapt to new threats and changes in the organizational environment.
For example, if you need a comprehensive approach to integrating security and privacy into your system development lifecycle, the NIST Risk Management Framework (RMF) is ideal. If you are focused on understanding adversary behavior and improving threat detection, the MITRE ATT&CK framework is better suited for developing advanced defense strategies based on real-world attack techniques.
Risk Treatment
Once risks have been identified, you need to determine how to address them. There are several options depending on their likelihood and impact that you can choose for treating risks. Below are some common approaches:
Risk Mitigation (Reduction): You can implement controls to reduce the likelihood or impact of a threat.
Risk Acceptance: You can acknowledge and accept the risk if it is deemed low enough or unavoidable, with no action taken to mitigate it when it falls within the organization's defined risk tolerance levels. This involves a conscious decision to accept the potential consequences of the risk based on a formal assessment of its likelihood and potential impact against established organizational risk criteria.
Risk Sharing/Transfer: You can share the risk by outsourcing security services to specialized providers such as MDR services, or through mechanisms like cyber insurance. It is important to note that the ultimate responsibility for a breach still lies with the organization. Although outsourcing and insurance can help manage risk and access specialized expertise, they do not eliminate the potential financial and operational consequences of a security incident.
Risk Avoidance: You can eliminate or prevent a risk altogether by avoiding risky activities like new partnerships, onboarding new supplier or using new technology.
Risk Mitigation
In this document, we will focus on risk mitigation, specifically those enabled by Bitdefender products and services, as it offers the most proactive approach to treating risks. While risk acceptance, sharing, and avoidance are valid strategies, effectively mitigating risk through controls helps address both the likelihood and impact of potential threats.
Risk mitigation involves implementing measures to reduce these factors, allowing you to focus on strategies that align with the formula:
Risk = Likelihood x Impact
For example, considering the risk of a data breach due to a ransomware attack, implementing a patch management program reduces the likelihood of the attack by minimizing vulnerabilities potentially exploited by ransomware. Leveraging a Managed Detection and Response (MDR) service reduces the impact by enabling rapid threat detection and response, minimizing the time attackers have to operate within your environment to encrypt data.
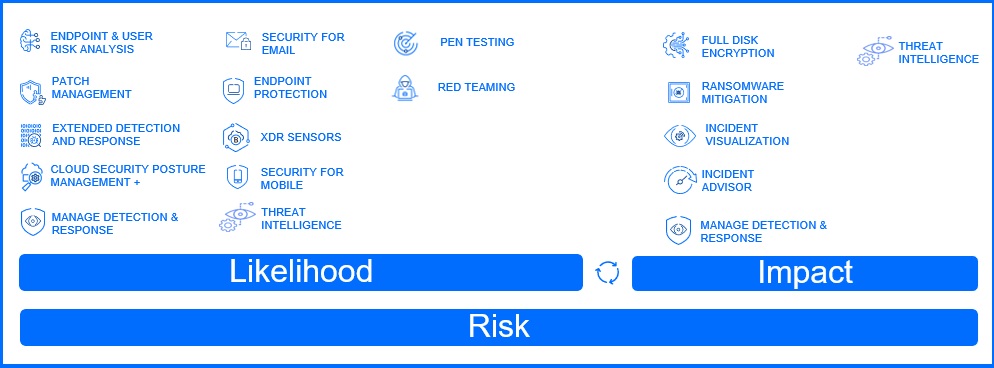
Reducing Likelihood
To reduce likelihood, you can start with users. Through training and awareness, you can train employees to recognize and avoid phishing attempts and social engineering attacks. However, even the best-trained people can fail when faced with sophisticated attacks, especially as LLMs make these attacks increasingly difficult to identify. Therefore, additional layers of protection that are able to recognize this kind of attack are crucial. You can help your users by implementing Email Protection to prevent phishing attacks, spam, and other email-based threats from reaching their mailboxes. It can recognize LLM phishing attacks, impersonation attacks, and malicious links, even in email attachments.
Strong authentication is essential for modern security. While passwordless authentication (like FIDO2) is the future, it may not be feasible for all organizations at this time. To enhance security, implement multi-factor authentication (MFA) to add an extra layer of security. For organizations with multiple applications, Single Sign-On (SSO) and federation can streamline the login process while maintaining security. Even with strong authentication, using a reputable password manager can help securely store and manage complex passwords.
Mobile devices are often an overlooked risk. Constantly connected to the internet and used for both personal and professional tasks, they become susceptible to data breaches, unauthorized access, and cyberattacks, posing a threat to sensitive information. Mobile security focuses on risk identification, threat detection, remediation, and reporting. Leveraging Mobile Threat Detection (MTD), it detects both known and unknown threats, including zero-day, phishing, and network attacks even when the mobile device is not connected to a corporate network safeguarding against a range of anticipated and unexpected threats.
Mobile Security Dashboard
You can reduce the likelihood of security incidents by conducting regular vulnerability scans and applying patches using Patch Management. Depending on your patch management strategy, you can utilize manual or automated patch deployment through predefined Maintenance Windows policies. For systems that cannot be patched, consider implementing additional security controls like network segmentation or increased monitoring to mitigate risks.
GravityZone Risk Management
While we have focused on user-centric measures, it is essential to remember that there can still be potential attacks due to misconfigurations in the operating system, computer configuration settings, and application vulnerabilities. For example, a publicly accessible application with a vulnerability that could lead to Remote Code Execution (RCE) can serve as an entry point for attackers to gain initial access to a system. Endpoint Risk Management is essential for identifying and addressing these misconfigurations using automatic or manual mitigation actions.
When threat actors use "Living off the Land" (LOTL) tactics, utilizing legitimate system tools and processes, they blend their malicious actions with normal operational activities. Proactive Hardening and Attack Surface Reduction (PHASR) proactively analyzes user and application behavior, creating behavioral profiles for each user-machine combination and comparing these profiles against known threat actor playbooks to prevent malicious activities. Instead of simply blocking entire applications, which could disrupt legitimate business operations, PHASR can implement granular, action-level blocking. For instance, while PowerShell itself might be necessary for administrative tasks, PHASR can identify and block specific high-risk PowerShell commands, such as those used for downloading remote files commonly associated with attacker playbooks. This reduces your attack surface and minimizes the risk of successful LOTL attacks before they even happen. Through a continuous learning cycle, it analyzes user actions, adapting to new user behaviors by modifying existing monitored rules or providing you with new recommendations.
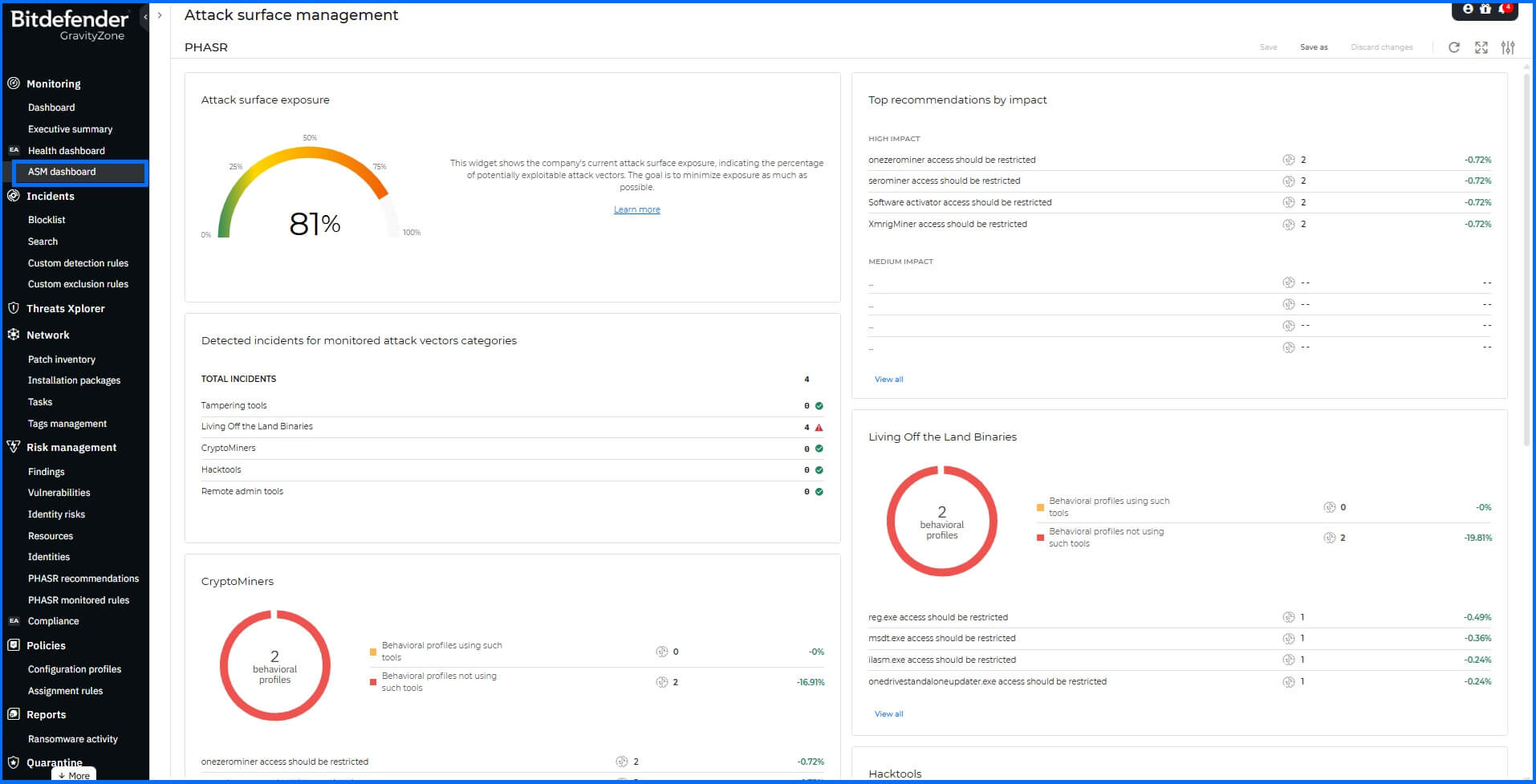
Bitdefender PHASR dashboard
You can't completely eliminate the risk, even with the best Risk Management strategy; you can only reduce it. Compromised devices can serve as entry points for further attacks, making their protection critical. You can safeguard internal devices by implementing Endpoint Protection Platforms (EPP). EPP offers multi-layered security, including malware protection, network protection, exploit protection, ransomware protection, and advanced features such as advanced machine learning technologies. It will safeguard them against a wide range of threats, including malware, ransomware, and other malicious attacks.
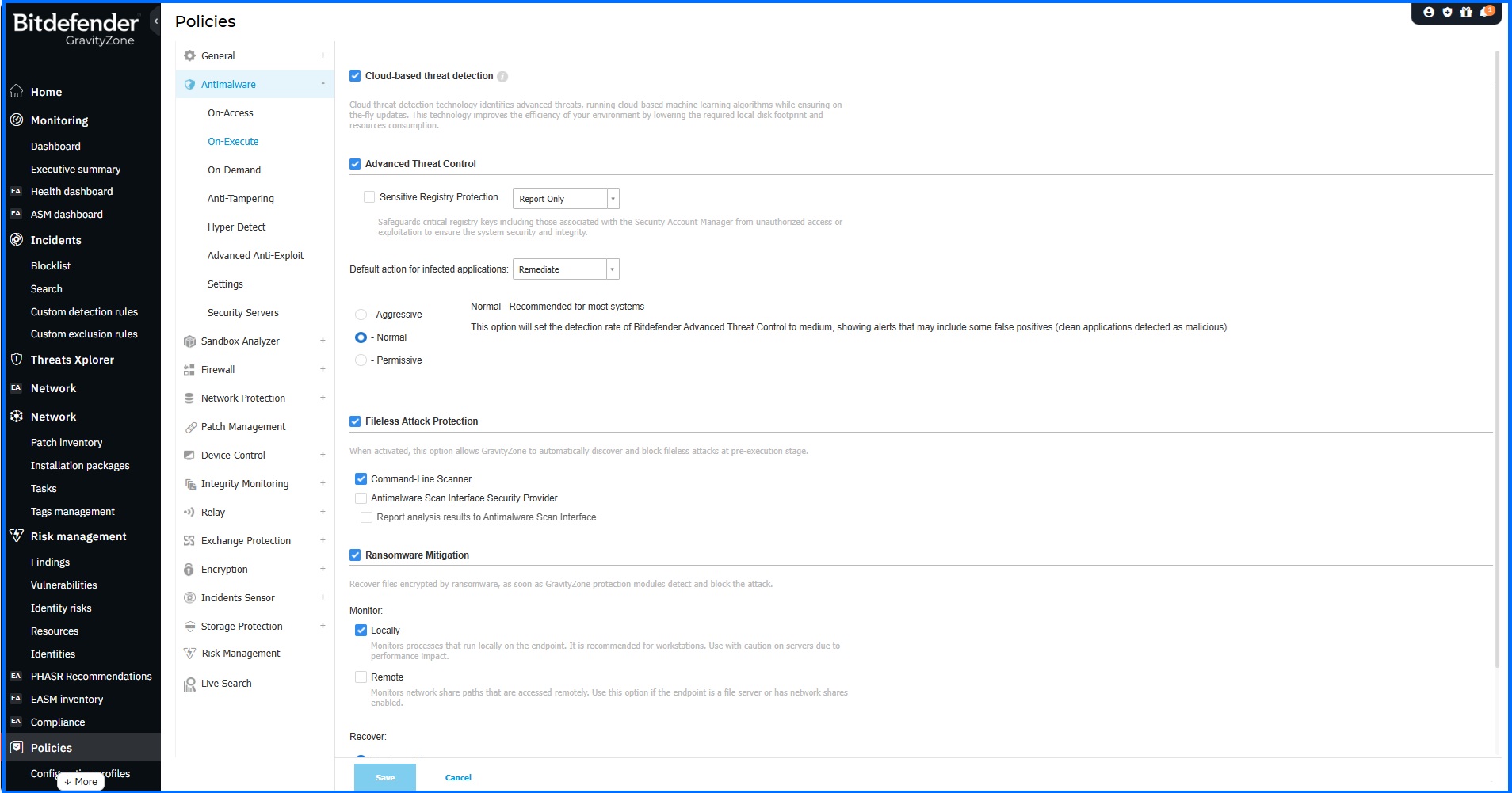
Bitdefender GravityZone Configuration Policy
Bitdefender EDR incorporates anomaly detection to identify unusual or suspicious activities that deviate from normal patterns of behavior within your IT environment. What is unique and important to highlight is that our custom machine-learning models used in anomaly detection are trained individually on each customer's system. This is not a mistake, your environment has its own unique machine-learning model, just as distinct as your IT environment itself. These models leverage data from endpoint sensors, correlating events, extracting, and processing features such as user login times, network connection durations, process creation patterns, and other relevant data, to create a behavioral baseline. Any deviation from your baseline can be considered potentially malicious. For instance, if a user who has never previously used PowerShell suddenly attempts to execute a PowerShell command, this could be flagged as an anomaly. All identified anomalies are communicated to you for further investigation and response.
The main reason for the evolution from Endpoint Detection and Response (EDR) to Extended Detection and Response (XDR) was to gain visibility beyond just the endpoints. With Sensors in GravityZone XDR you can actively monitor your IT infrastructure, including devices, networks, cloud environments, identities, and productivity applications, for potential threats such as ransomware attacks. Sensors enhance your visibility across the entire attack lifecycle, starting from the initial point of compromise and extending to all impacted resources. For example, XDR can provide you with a comprehensive view of an attack, starting from a phishing email that's used to steal user credentials. It can track the attacker's actions as they leverage these credentials to gain privileged access, move laterally within the network, and ultimately encrypt sensitive data or exfiltrate it to external systems.
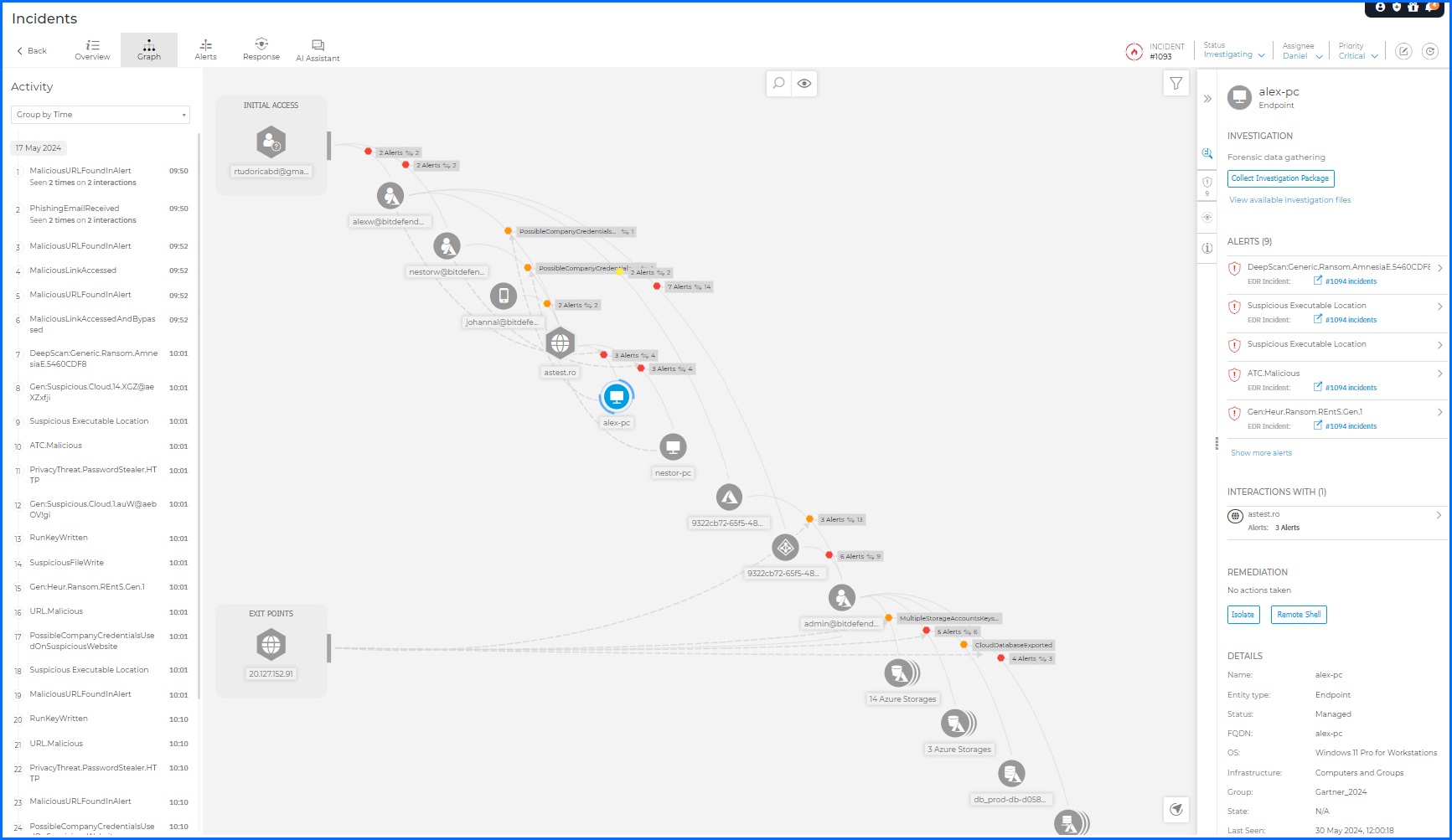
Bitdefender GravityZone Extender Root Cause Analysis
As organizations increasingly operate in hybrid environments, combining on-premises infrastructure with cloud services, it is crucial to address the unique security challenges associated with this shift. The adoption of cloud computing offers organizations numerous benefits such as scalability, flexibility, and cost-effectiveness however migrating to the cloud also introduces new security risks such as misconfiguration or excessive rights that can lead to data exposure or unauthorized actions. For instance, a common misconfiguration in cloud environments is leaving storage buckets publicly accessible. This can expose sensitive data to unauthorized individuals. Cloud Security Posture Management (CSPM+) plays a vital role in addressing these challenges by continuously monitoring configurations to identify and address misconfigurations and permissions within your cloud environment.
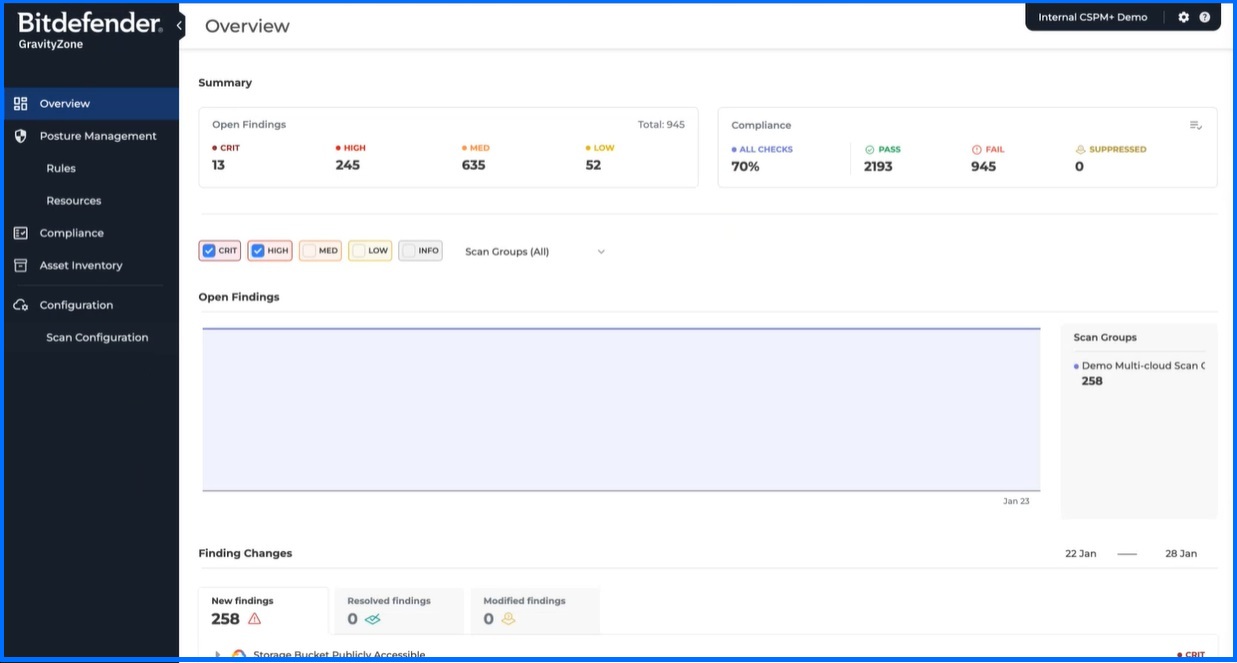
Bitdefender Cloud Security Posture Management
While internal security measures are essential, it is equally important to address the security of publicly exposed assets. These assets can have weaknesses, such as open ports, exposed services, and vulnerabilities. This is like leaving a back gate unlocked, making them a prime target for attackers who constantly scan for exposed systems to leverage publicly accessible information to identify vulnerabilities and gain initial access to your systems. For example, an attacker could discover an exposed database server on your network and exploit a known vulnerability to gain unauthorized access to sensitive data. To reduce the external attack surface, you need comprehensive visibility across your external assets before attackers can exploit them. External Attack Surface Management (EASM) continuously monitors your external-facing assets such as web applications, network infrastructure, and cloud services to identify and address vulnerabilities before they can be exploited.
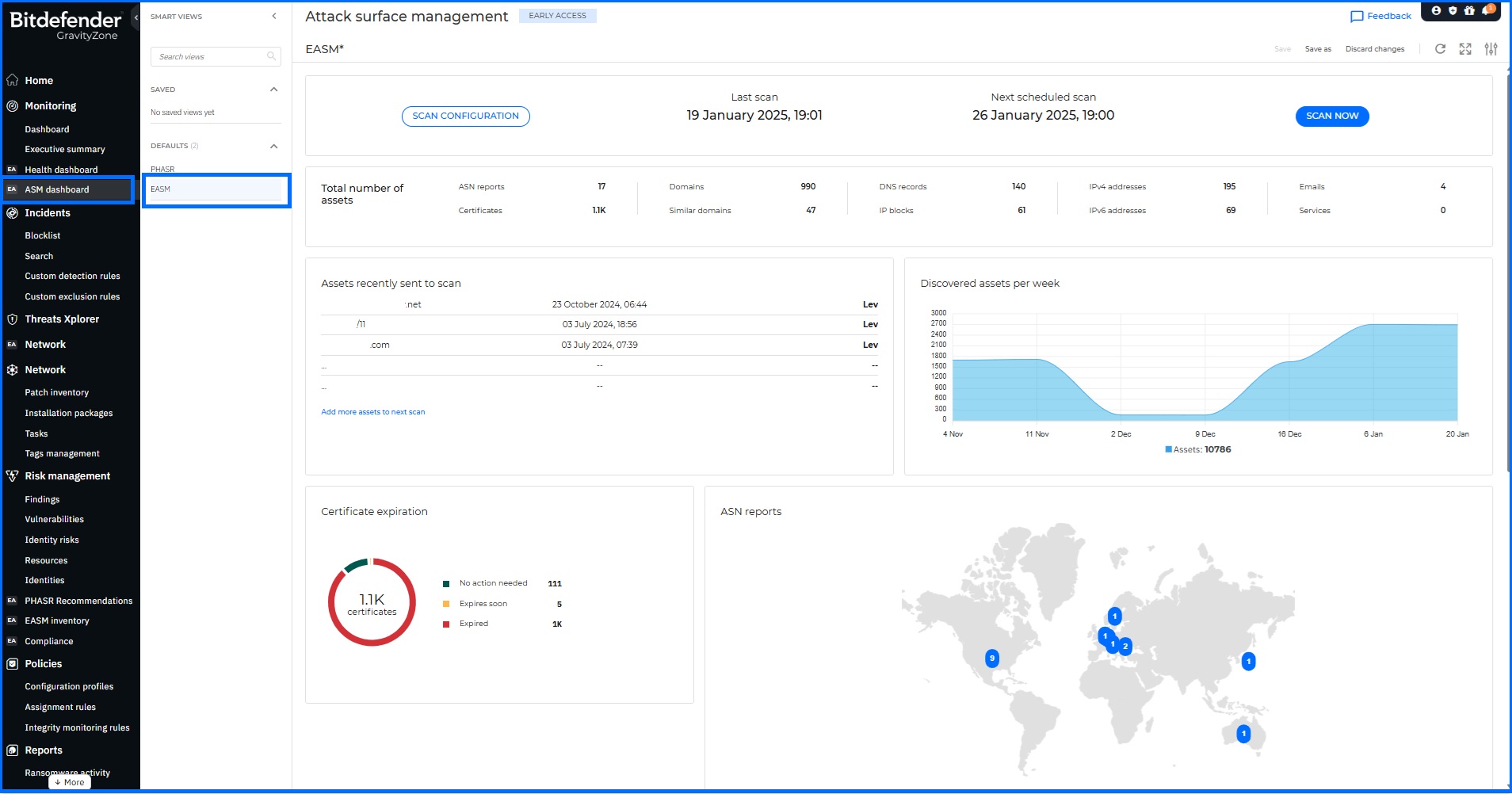
Bitdefender External Attack Surface Management
Risk analytics provides a holistic view of organizational risk by aggregating and analyzing data from various sources. This enables the identification of patterns, trends, and potential threats, including attack paths. By correlating findings across User Risk Management, Endpoint Risk Management and Cloud Security, it pinpoints root causes of incidents and reveals related security risks. For example, if an incident resulted from a user's credentials being used in unencrypted communication, Risk Analytics would report this along with other identified root cause risks and the top five most severe risks. This information can be used to reduce the likelihood of similar incidents by implementing measures like mandatory multi-factor authentication and securing communication methods through encryption.
Our goal is to correlate more findings, for example vulnerabilities and EASM to trace the sequence from initial discovery to lateral movement and data exfiltration. Also, by correlating identities based on their attributes, we can create a comprehensive risk profile across the entire environment. Network Anomaly Detection will enable us to identify and prevent network-based attacks and analysis also considers the involved users and relevant files.
If you are using our Managed Detection & Response (MDR) service, the Cyber Threat Intelligence (CTI) team, which is part of it, also helps mitigate the risk. The CTI team assesses information gathered from a wide variety of sources including various cyber intelligence gathering tools, scouring the dark and deep web, gathering data from various law enforcement organizations around the world, gathering threat information from the Bitdefender Labs team, and reviewing information from various reliable news authorities. Furthermore, the CTI team actively leverages Threat Intelligence to monitor for credential leaks/email exposures or monitor for domain abuse or insecure code repositories. Their findings are discussed with the MDR SOC analysts and action plans are custom tailored to your environment, the businesses’ field of activity, and details of the identified potential threat.
Bitdefender MDR
While the above security controls provide a solid foundation for mitigating risks, a proactive approach to security also involves actively hunting for potential threats. Offensive services, are designed to proactively assess security gaps in your environment, whether on-premises, cloud, or hybrid. Offensive security services, conducted by ethical hackers who mimic real-world attacks, go beyond simply testing your prevention. They stress-test your entire security posture, prevention, protection, detection, and response mechanisms. Penetration Testing identifies vulnerabilities and risks by simulating real-world attacks, helping you understand your security posture of specific assets. Red Teaming takes it a step further by simulating real-world attacker behavior across interconnected assets, allowing you to test your detection and response capabilities against advanced threats like ransomware.
Reducing Impact
Even with the most robust security measures in place, it is inevitable that threat actors will eventually find a way to breach your defenses. While we can strive to minimize the likelihood of a successful breach, we must assume that an incident will occur and focus on promptly detecting and responding to threats.
One of the most effective ways to reduce the impact of a data breach is to encrypt sensitive data at rest. Without encryption, sensitive data is vulnerable to theft. For example, if a laptop containing sensitive data is stolen, the thief could potentially access the information. Full disk encryption of hard drives, external drives, and other storage systems provides you a robust defense against data breaches, significantly reducing the potential impact of unauthorized access to sensitive information. It also helps you meet some of the regulatory compliance requirements such as GDPR and HIPAA.

Bitdefender GravityZone console
When threat actors gain access to your system, they can execute encryption software to lock your data and demand a ransom. The Ransomware Mitigation module monitors endpoints and blocks processes that attempt to alter the data. This technology encompasses three primary areas: operating system level, files, and cloud support. For example, it analyzes specific portions of the file in usage and applies statistical formulas, including entropy and chi-square tests, to detect indications of file encryption. When a ransomware attack is detected and blocked, it will report to you information about the user session on the endpoint and the files that have been impacted, with the possibility of file restoration either manually or automatically. The backup process is performed in real time and triggered only when necessary. Ransomware mitigation technology does not rely on the shadow copy mechanism for backup; instead, we developed our own internal mechanisms. This approach protects data, as malicious actors often target shadow copies and backups before encryption and ensures that there is minimal impact on the overall system performance.
When a threat is detected, an incident is automatically created to initiate a forensic investigation. Understanding how an attack occurred is crucial for containing the threat and preventing further damage. With Incident Advisor, you can significantly reduce the time required to investigate and contain threats. By correlating data from multiple sources and presenting it in a clear and concise format, Incident Advisor streamlines the investigation process, allowing you to focus on identifying the root cause of the incident and taking timely corrective actions. This comprehensive overview of the incident, including its cause, effects, and potential risks, enables you to make informed decisions and implement effective incident response action for example, you can block suspicious AD users and isolate the host where the incident started.
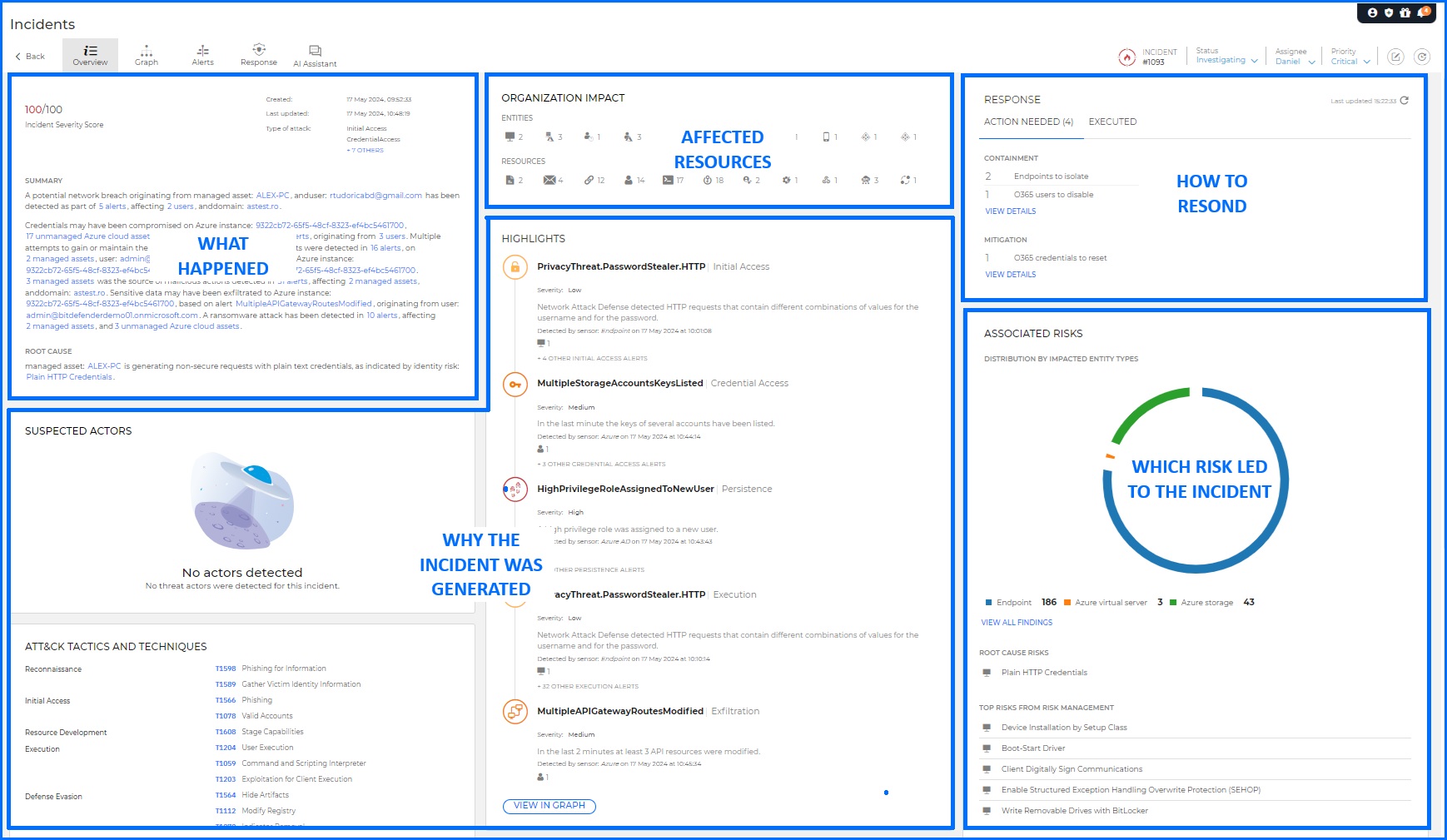
Bitdefender GravityZone Incident Advisor
Additionally, you can gain valuable insights by leveraging Threat Intelligence when a suspicious file or connection is detected, or a threat is identified. All files can be analyzed to check their reputation, and if it is an unknown file, it can be sent to a sandbox for further analysis. Using IOCs, you can search for the threat actor and, knowing their TTPs, create custom detection rules to isolate endpoints when specific files, processes, or connections are detected. Threat intelligence can also be used to search for threat actors targeting your industry. This proactive approach allows you to create custom detection rules in advance based on the IOCs assigned to threat actors. You can also use live search functionality based on the OSquery to create finely tuned and organization-specific detection patterns. For example, if a YARA rule is designed to detect a specific malware signature within files, on-access scanning would trigger an alert whenever a file with the matching signature is accessed or executed in real-time by any user or process.
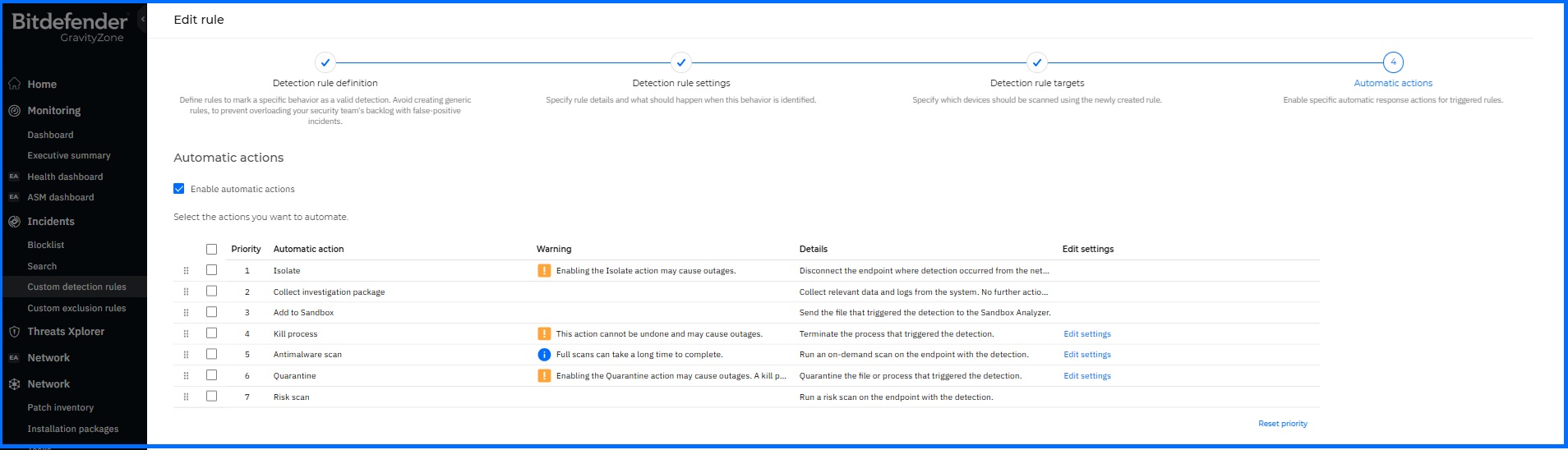
Bitdefender Custom Detection Rules
A key strategy for reducing the impact of a cyberattack is to leverage a Managed Detection and Response (MDR) service. If you are running a business but lack a dedicated security team, MDR provides invaluable assistance. By partnering with an MDR team, you can effectively leverage expert security knowledge and resources to enhance your incident response capabilities and minimize the impact of cyberattacks, even with limited in-house security resources. MDR teams actively hunt for threats, including advanced threats, zero-day exploits, and insider threats, that may have evaded traditional security controls. They can quickly detect and respond to security incidents, minimizing dwell time and reducing the potential damage caused by attackers. Furthermore, MDR teams conduct in-depth investigations to identify the root cause of incidents and collect forensic evidence, while recovery and remediation efforts focus on restoring affected systems. To further mitigate the financial consequences of a successful attack, Bitdefender includes a Cybersecurity Breach Warranty as part of its MDR and MDR PLUS services. This serves as a reactive risk-transfer tool, providing financial assistance to offset recovery costs, legal liabilities, and non-IT business expenses, ensuring that an organization’s financial stability is preserved even after a critical incident.
Clear responsibility and ownership during each phase of the incident are crucial. The security team, typically led by the CISO, coordinates with IT, legal, and other departments to ensure an effective response. A well-defined Incident Response Plan outlines clear processes and responsibilities, ensuring everyone knows their role. The key phases include:
Preparation: Set up the tools, training, and systems necessary for incident handling. Establish clear processes and assign ownership.
Detection: Quickly identify threats using monitoring tools such as XDR or MDR to mitigate damage early.
Containment: After detection, immediately contain the threat to limit its spread.
Eradication: Eliminate the threat from the network or system.
Recovery/Hardening: Restore normal operations while addressing the root cause to prevent recurrence.
For example, imagine a scenario where a phishing email compromises an employee's account, allowing attackers to gain initial access to the network. With an MDR service in place, this could be detected rapidly, enabling security teams to quickly isolate the compromised system and prevent further lateral movement within the network.
Incident response works in tandem with Business Continuity Planning (BCP) to ensure operational resilience during and after an incident. Minimize downtime by identifying critical business functions and ensuring backup systems are ready. Assign clear ownership of continuity tasks to relevant teams. Regular testing and updates to both the incident response plan and BCP enhance resilience. Ensuring teams are prepared to act quickly reduces financial and operational impacts. Conduct a post-incident review to identify areas for improvement. Document lessons learned to update the existing incident response plan and better mitigate future risks.
Demonstrating the Value of Cybersecurity
For security leaders, including Chief Information Security Officers (CISOs) and Chief Information Officers (CIOs), effectively demonstrating the return on investment of cybersecurity to the executive team and stakeholders is key to ensuring that security is seen as an investment rather than a cost.
For example, by calculating the cost of downtime you can provide tangible evidence of how security projects save the organization. Here is how you can estimate costs:
Revenue Loss: You can estimate the average revenue generated per hour or day and calculate the loss associated with a complete business shutdown due to a cyberattack.
Cost of Incident Response: You can account for the costs of incident response teams, forensic analysis, legal fees, and regulatory fines.
Reputational Damage: You can estimate the loss of trust by considering the potential customer and market share lost, although it can be difficult to quantify.
By using this and similar metrics cybersecurity investments can be framed as cost-saving measures that reduce the likelihood of costly incidents.
A key aspect of demonstrating cybersecurity value is measuring its effectiveness by tracking performance and showing the financial and operational impact of risk reduction. You can for example define the following criteria:
Mean Time to Detect (MTTD): You can measure how quickly threats are identified.
Mean Time to Respond (MTTR): You can measure the time it takes to detect and mitigate security incidents.
Patch Management Effectiveness: You can track systems and applications that are patched within a defined time frame.
Compliance Support: You can track adherence to regulatory and industry standards, such as ISO 27001, NIST, or GDPR.
Tools such as the Bitdefender GravityZone console provide you with a centralized dashboard that tracks these key metrics. It offers real-time insights on threat detection, patch management, and overall security posture. This data can be represented as a report for executives, helping you quantify the value of cybersecurity efforts in business terms. By presenting metrics such as faster incident response times or higher compliance scores, you demonstrate how the security program aligns with business objectives, such as reducing operational downtime and protecting revenue.
If you are unsure how to effectively leverage security metrics (Key Performance Indicators or Objectives and Key Results), collaborating with a third-party security services provider can provide valuable insights.
Regulatory Compliance
Regulatory compliance goes beyond legal obligations; it is a strategic approach to managing cyber risks and demonstrating the value of cybersecurity investments. You can use these regulations to identify, assess, and mitigate risks. Several key regulations and standards can guide you in establishing right cybersecurity practices. For example:
General Data Protection Regulation (GDPR): GDPR is EU regulation that requires organizations to protect the personal data and privacy of EU citizens. It includes requirements for data processing, consent, data subject rights, and breach notification.
Health Insurance Portability and Accountability Act (HIPAA): HIPAA is a U.S. regulation that requires healthcare organizations to protect patient health information. It includes provisions for securing electronic medical records, ensuring patient privacy, and notifying individuals in the event of a data breach.
NIS Directive: NIS and NIS2 2 is the EU’s cybersecurity directive aimed at improving the security of networks and information systems across critical sectors. It establishes measures for risk management, incident reporting, and cooperation between EU member states to enhance the overall resilience of critical infrastructure.
Digital Operational Resilience Act (DORA): DORA is an EU regulation that aims to strengthen the operational resilience of financial institutions. It introduces requirements for identifying and managing risks, testing resilience, and reporting incidents.
GravityZone Compliance Manager provides you with real-time evaluation of endpoint compliance posture through built-in mappings that link requirements from compliance standards to technical controls on your endpoints. Each finding related to compliance standards or frameworks comes with clear, actionable remediation techniques, including manual and automatic options. While specific threats might require manual intervention, you will find detailed, step-by-step guidance for fixing the risk in the dedicated Risk Mitigation section. For issues that can be resolved automatically, with a single Fix risk button, you can simply create a task to mitigate them by changing the configuration, ensuring efficient and timely resolution of compliance gaps. Audit-ready reports can be used to demonstrate the effectiveness of your risk reduction initiatives for external auditors or internal management.
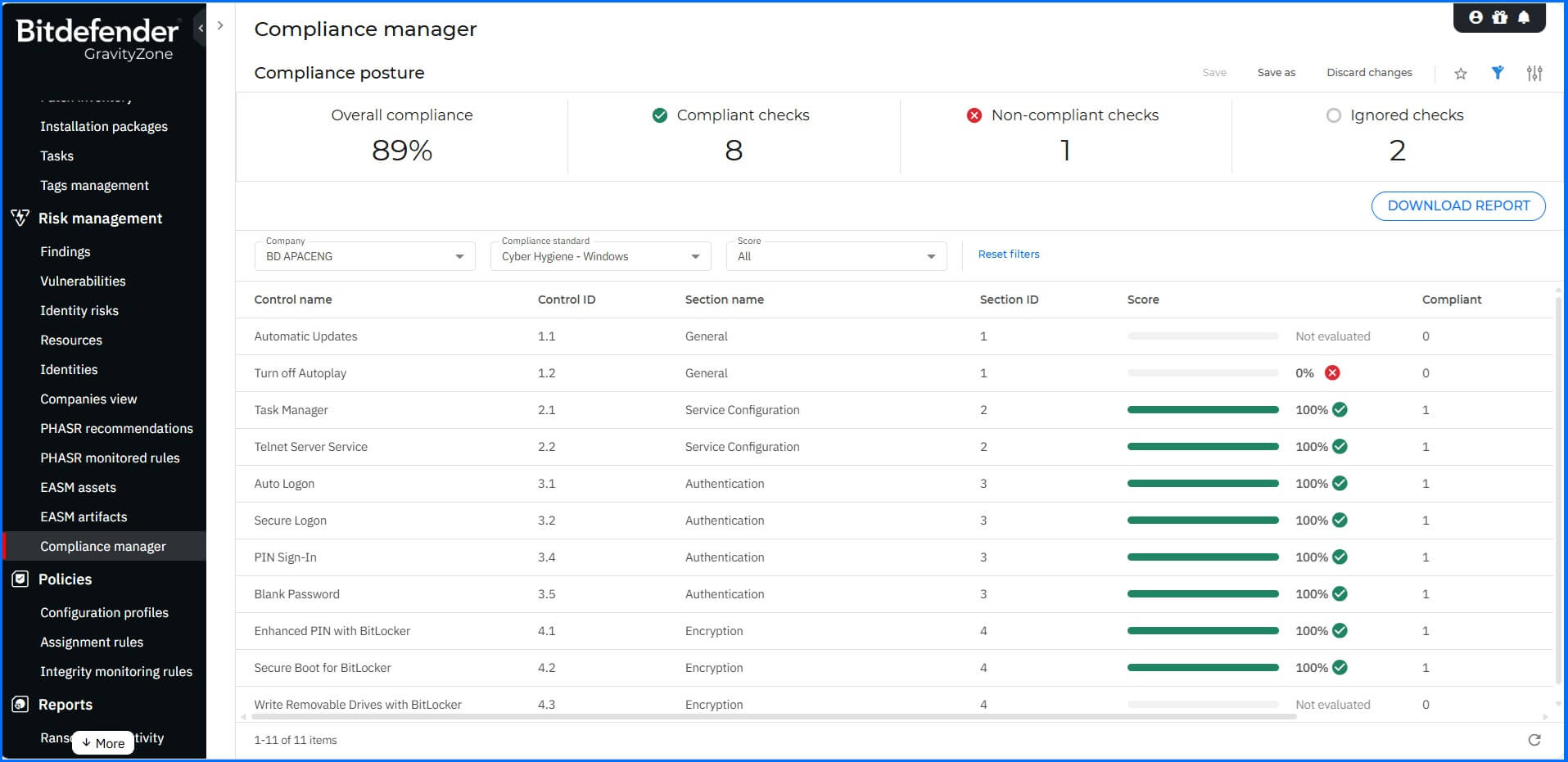 GravityZone Compliance Manager |
If your organization is required to comply with these or similar regulations, it often mandates additional audits to ensure regulatory requirements are met. Key considerations for audit preparation include Penetration Testing and Red Teaming.
If you need comprehensive compliance support—from gap analysis and improvement recommendations to accreditation assistance—consider partnering with a third-party security services provider to leverage their expertise and enhance your security posture.
Conclusion
Cybersecurity risk management is not a one-time project but a continuous process that evolves with your business. By adopting a structured approach—grounded in risk calculation, strategic mitigation, incident response, and compliance frameworks—your organization can better protect its assets and maintain operational resilience. Begin by evaluating your current cybersecurity posture and considering partnerships with security service providers to ensure a proactive, comprehensive defense against threats.