Incident Investigation and Forensics - Bitdefender TechZone
Bitdefender GravityZone provides an efficient solution for incident investigation and response. With Extended Root Cause Analysis and a unified view of incidents, administrators and security teams minimize response time, understand attack chains, and enhance cybersecurity posture.
While not all attacks can be stopped, you should focus on detecting incidents that manage to evade prevention and protection technologies.
An incident refers to any unplanned event that disrupts normal operations and causes or has the potential to cause damage or harm to your organization's assets, services, or data. Incidents can be caused by a wide range of factors such as software bugs, hardware failures, cyber-attacks, or human errors.
Incident investigations provide insights into the vulnerabilities and weaknesses exploited during an attack. This process helps you develop a historical record of incidents, which can be used to identify trends, patterns, and recurrent threats. Understanding how an attack occurred is crucial for containing the threat and preventing further damage. It is also important in the learning process from past experiences and contributes to improving your overall safety and security by developing strategies to minimize their impact.
Analyzing security incidents can be overwhelming. The task of sifting through extensive data from various sources without clear connections significantly reduces your response time and the likelihood of stopping the spread of an attack. With the GravityZone Incidents functionality, you gain access to a consolidated platform that streamlines the analysis process by providing a unified view.
Incidents
The Incidents functionality helps you filter, investigate, and act on all security events detected and generated for the managed company in the last 90 days. These incidents are generated through various detection layers, including standard EDR/XDR sensors, custom detection rules, and YARA rules applied during On-Access scanning.
You can distinguish two types of incidents:
The Endpoint Incidents displays all suspicious incidents detected at the endpoint level (EDR), that require your investigation and upon which no action has been taken yet.
Organization Incidents consolidates all incidents and detections into a single panel. When possible, the correlation engine correlates host-level endpoint incidents (EDR) from all endpoints. For the XDR subscription, correlation is performed alongside attacks identified by Sensors.
The All Incidents Investigation tab provides a human-readable summary of all incidents, where you can customize smart views according to your needs or use default ones. To aid in classification and strategy, alerts within these incidents are automatically mapped to MITRE ATT&CK techniques.
To see a live walkthrough of these capabilities in a pre-configured environment, you can explore our XDR Demo Incident article.
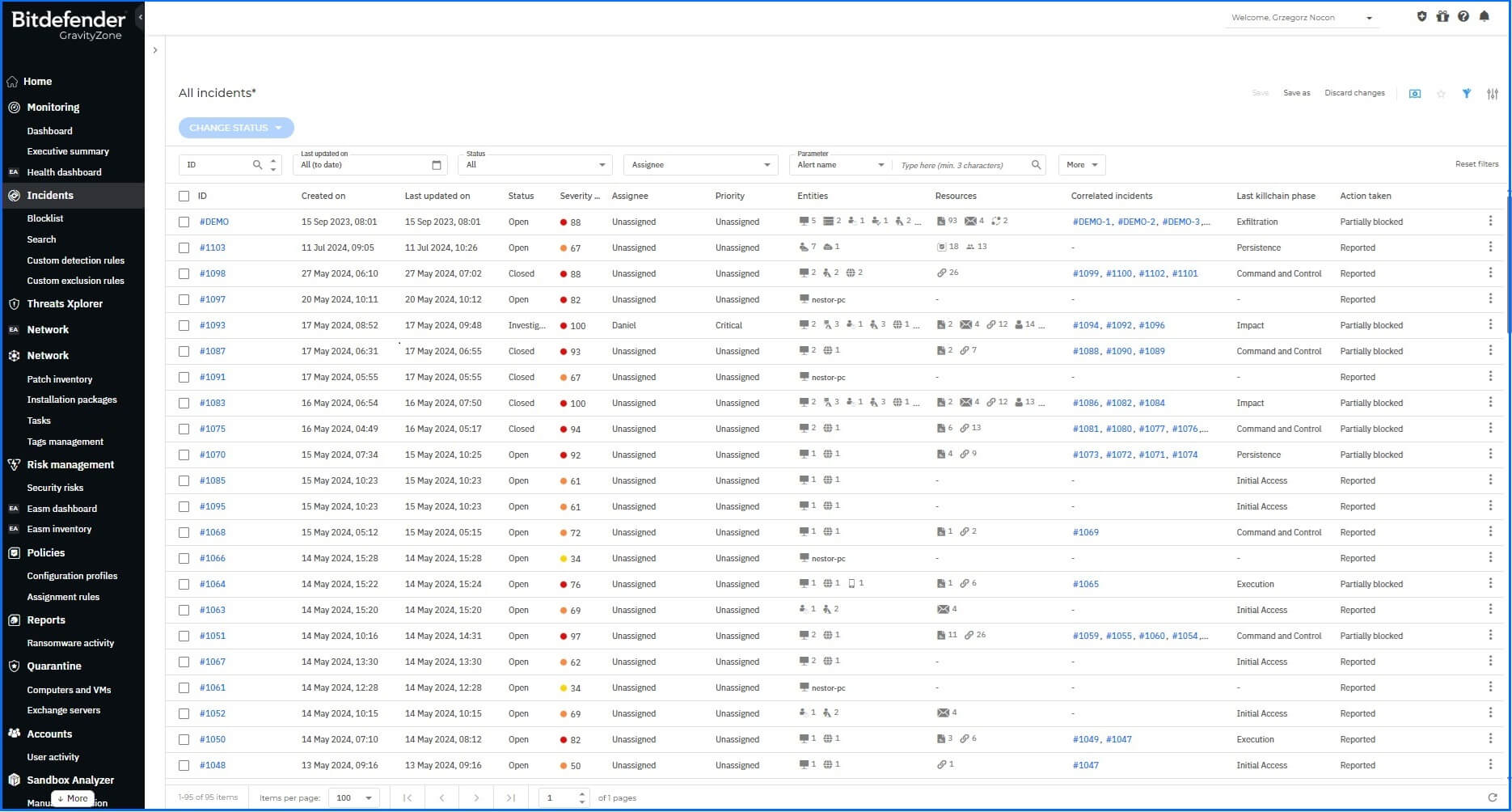
Bitdefender GravityZone Incident section allows security teams to check all Incidents at a glance.
Once incidents are correlated, only the root entry remains, with an ID of child incidents correlated with the one displayed in the grid.

Bitdefender GravityZone root entry of correlated incidents.
To help manage your workflow, you can update incident statuses (e.g., Open, Investigating, False Positive, or Closed) and apply these changes to all correlated events. To further refine detection and minimize noise, directly from the Incident section, yous can add EDR Exclusions. Detailed information about Custom exclusion rules can be found in the Bitdefender Support Center here.
Detailed information about Incident Investigation flow can be found at our Bitdefender Support Center here.
Incident Advisor
GravityZone Incident Advisor was designed to minimize the time you require to investigate and contain threats. It is available as a default landing page when you select an incident and provides an intuitive and visually comprehensive overview of information for key questions:
What happened: A short summary and information about the incident severity score.
Why this incident was generated: It includes mapping to MITRE ATT&CK tactics and techniques used during the incident, along with the Root Cause Analysis.
How this incident has affected the organization: This covers all affected resources based on the information from endpoints and Sensors.
How to respond to minimize the business impact: Provides single-click response across the organization. All the response actions were detailed in the Threat Response article.
Which risk led to the incident: Pinpoints the root causes that led to the incident and reveals all related security risks linked to incident-related entities.
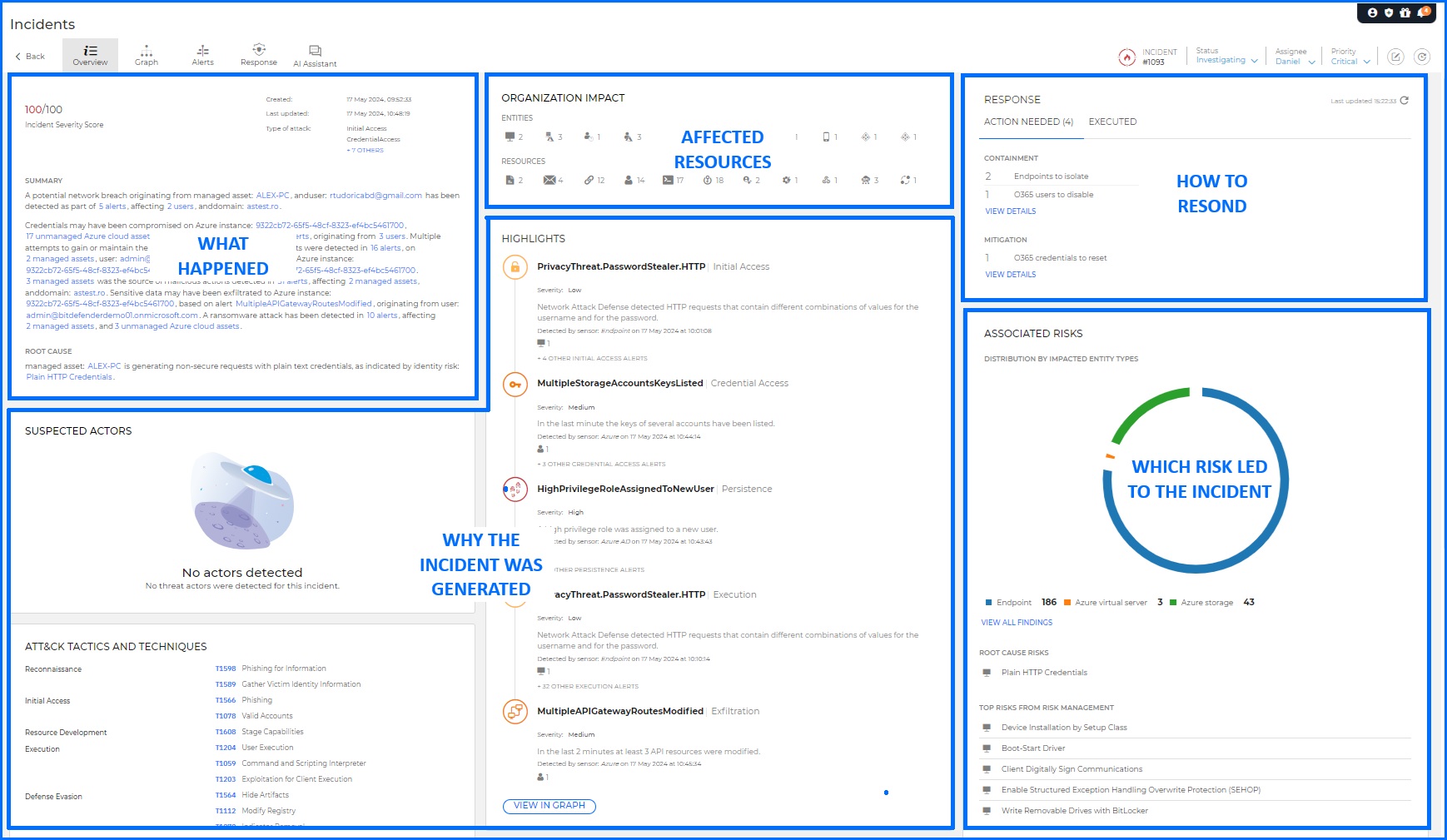
Bitdefender GravityZone Incident Advisor allows security teams to check all the key details about the particular incident.
Incident Advisor correlates data from multiple sources, presenting it in a format that minimizes the time you need to investigate and respond to the incident. You can export a selected incident into PDF format. This report includes all the information that's included in Incident Advisor, making it a valuable resource for your internal reporting and compliance.
Root Cause Analysis
The Root Cause Analysis provides an interactive graphical map of the investigated incident. This map highlights the critical path, which is the exact sequence of events that triggered the attack. It also shows all other elements involved, allowing you to see the bigger picture but keeping the critical path in focus. By visualizing the flow of the attack and the relationships between processes and file system operations, you gain a deep understanding of how the attackers operated. This valuable insight enables you to take decisive action to stop the attack in its tracks and prevent future breaches.
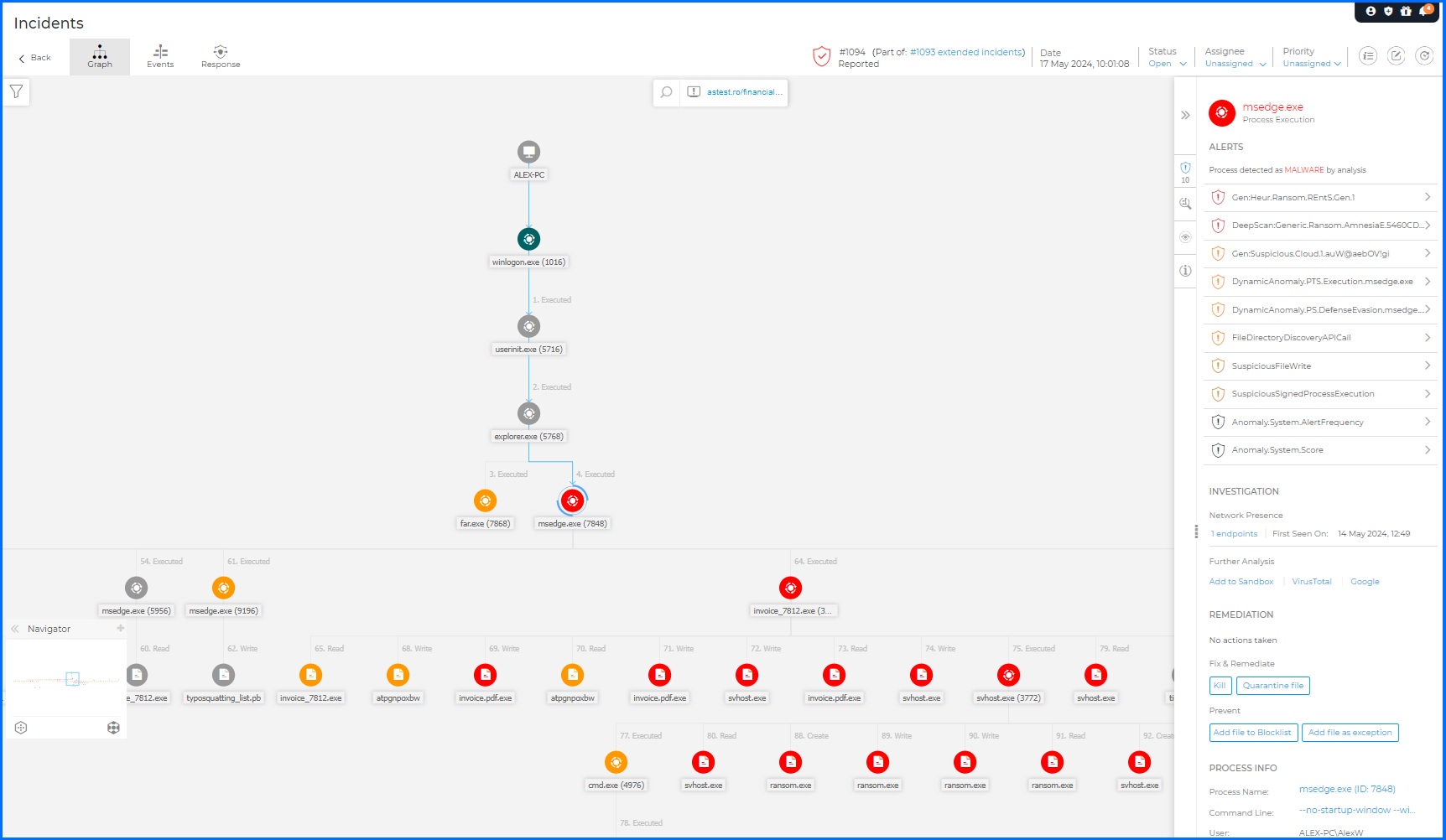
Bitdefender GravityZone Root Cause Analysis allows security teams to check all milestones during incident execution.
Extended Root Cause Analysis
An in-depth investigation of the security incident is available via a visual graph. The Graph tab presents a dynamic visual representation of your ongoing incident investigation, offering a detailed activity timeline. It illustrates the sequence of correlated sources, data, context, and events caused by external agents, whether they have already occurred or are still active in the environment. You can find relationships and directions of communication across users, endpoints, cloud workloads, and files.
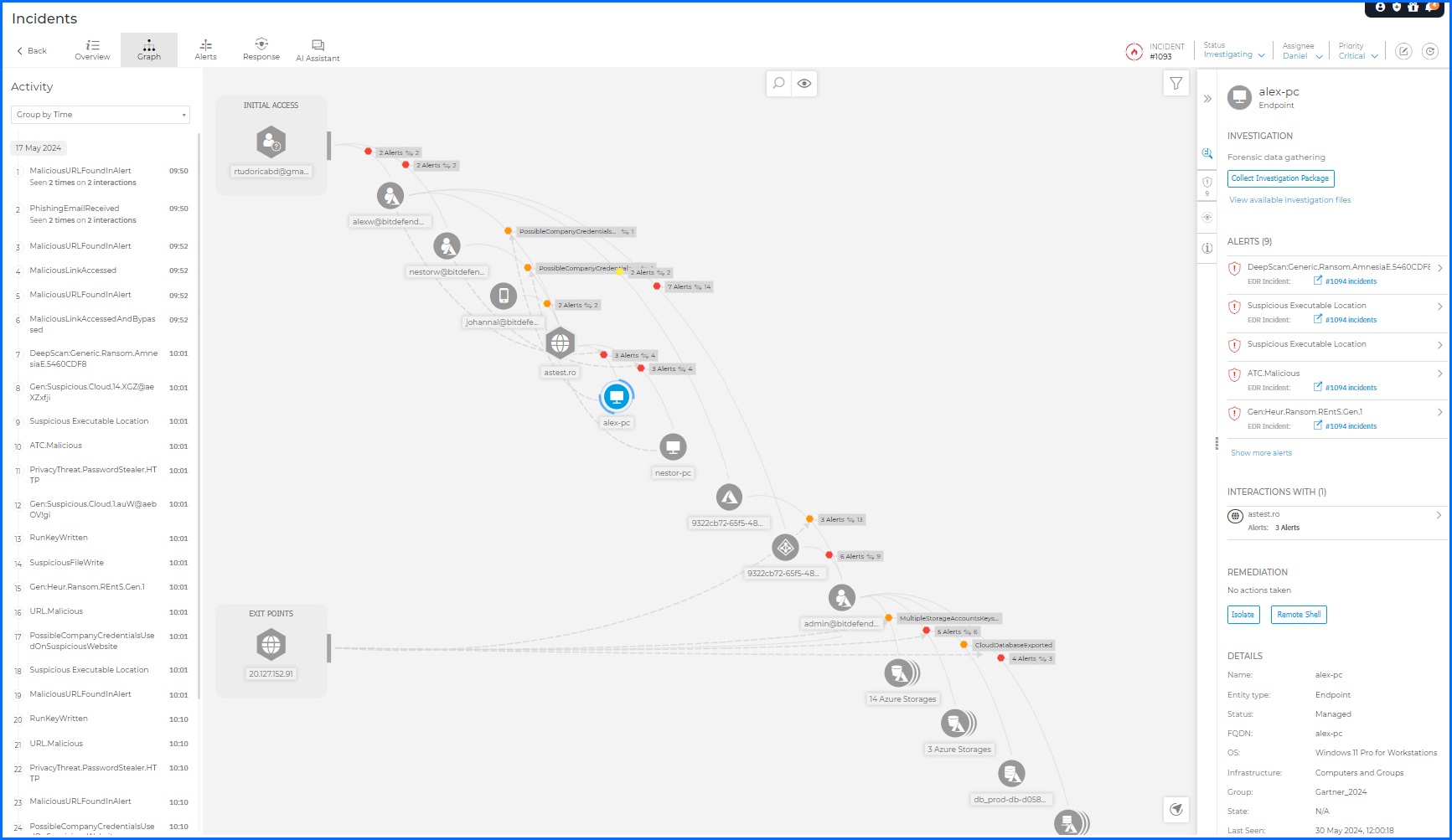
Bitdefender GravityZone Extender Root Cause Analysis allows security teams to deeply investigate each single incident.
The portal user experience is rich with visualization and easy for you to pivot from fact to information within a report. Selecting, for example, the initial access stage will automatically highlight all elements and connections occurring at this stage of the incident. You can use the Alerts panel to review a chronological sequence of all events, helping you understand exactly when each malicious step was taken.
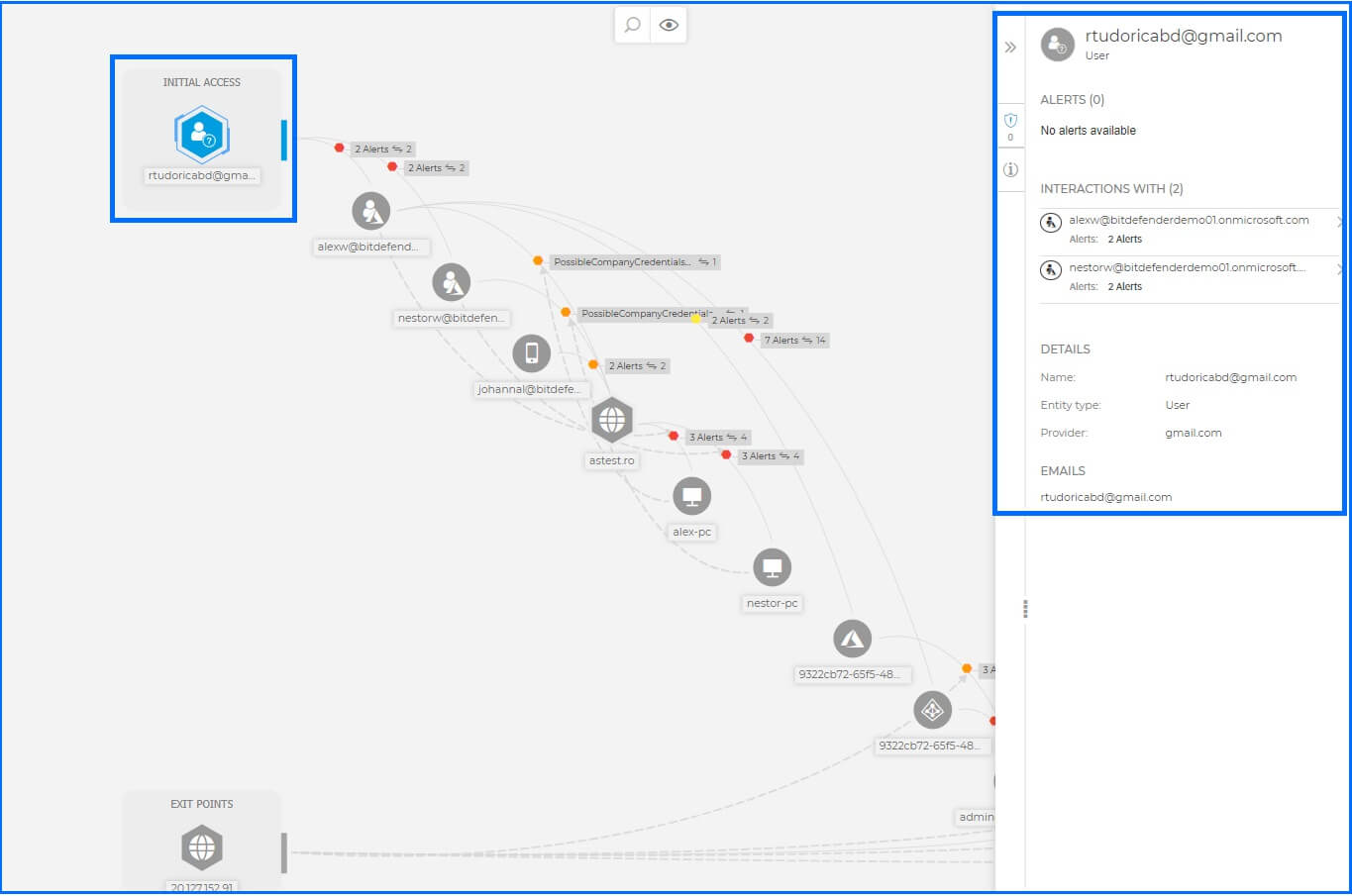
This allows you to understand the attack chain and determine the specific Tactics, Techniques, and Procedures (TTPs) employed by the threat actor. The comprehensive insights you gain from Extended Root Cause Analysis empower you to launch targeted Responses and enhance defenses against similar threats, enhancing your cybersecurity posture.
Response
For each incident, administrators have access to the Remediation section, which includes actions requiring immediate attention, actions that have already been executed, or actions that have been dismissed. The available actions vary based on the type of Sensors the administrator has.
In the case of Endpoint Incidents, you can take immediate action by isolating the endpoint, killing malicious processes, or blocking suspicious files. When combined with a Patch Management subscription, you can also install patches to reduce the attack surface by minimizing active vulnerabilities. For organizations utilizing Sensors like the Active Directory Sensor, you can disable compromised AD accounts or force password resets. Additional information about responses and available actions is detailed in the Threat Response article.
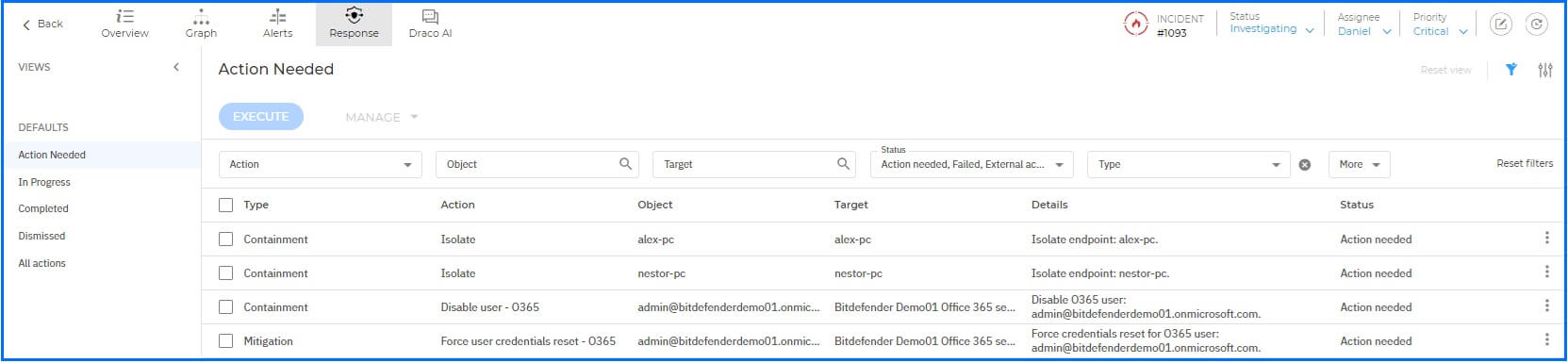
Bitdefender GravityZone Response section allows security teams to take any action needed.
Remote Connection
For Windows-based endpoints, the security team can further investigate by establishing a Remote Connection directly from the incident details panel. This feature allows you to open an EDR Terminal Session to perform actions on the affected system. These sessions use custom-built shell commands designed for security tasks, providing a predefined set of commands to remediate the threat directly on the operating system.
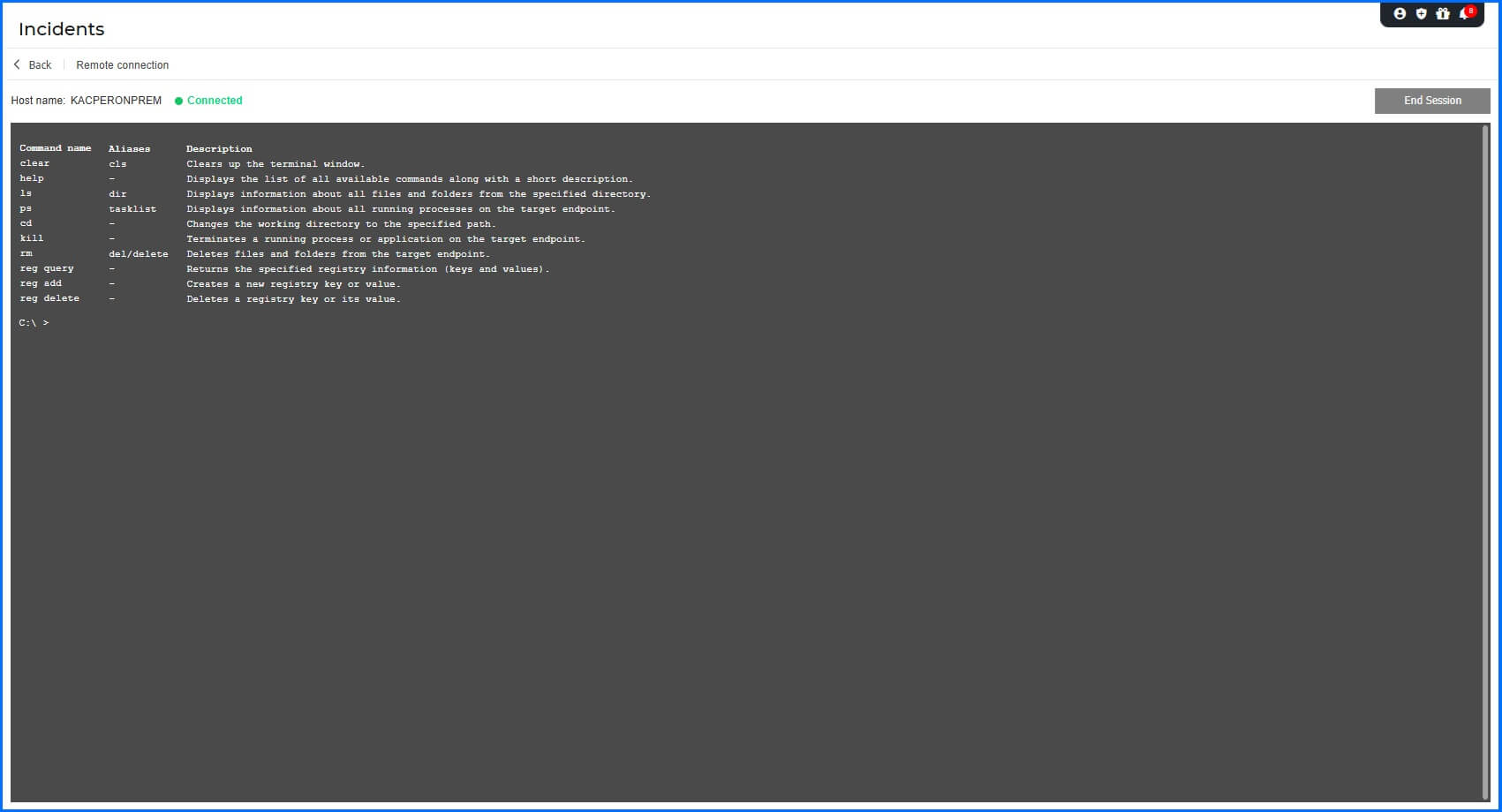 |
For example, you can use the ps or tasklist command to identify a suspicious running process and obtain its Process ID (PID), then immediately use the kill [PID] command to terminate the threat.
Detailed information about terminal session commands can be found in the Bitdefender Support Center here.
Forensics
To collect extra information from endpoints affected by an incident, you can create an Investigation Package with forensic data. This functionality is available for Windows, Linux, and macOS computers. Detailed information about the collected data, depending on the operating system, can be found on our GravityZone Support Center page and the instructions on creating an investigation package.
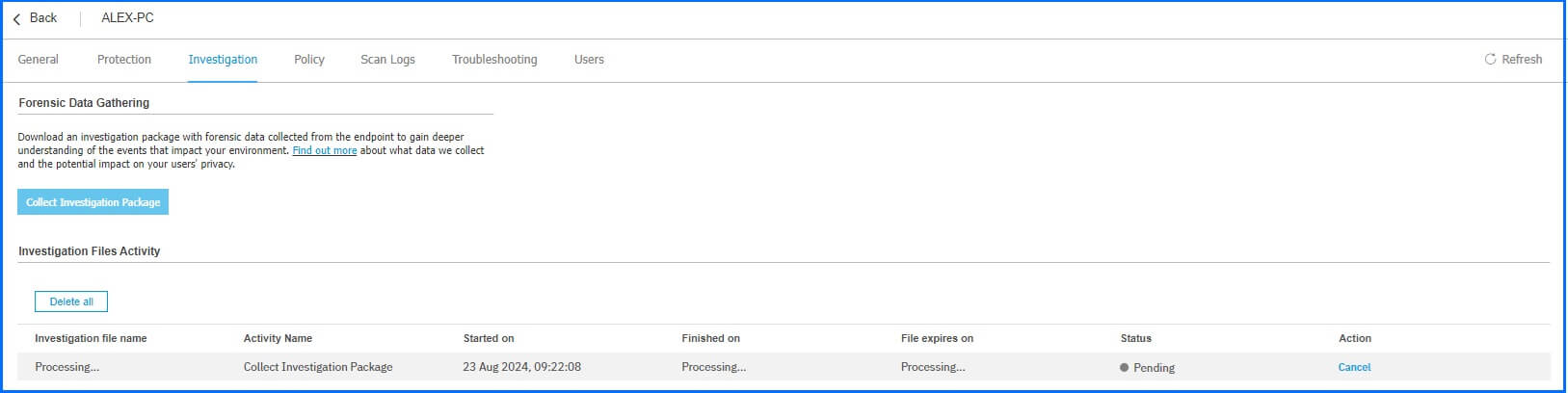
It is worth noting that investigation files have a data retention period of 24 hours. All files are encrypted in transit, at rest, and in use.
Hands-on Scenarios
The following scenarios demonstrate how you can solve specific challenges using the forensic and investigation capabilities of GravityZone.
How do I quickly understand and report what happened?
When a high-severity incident occurs, you are often under pressure to provide an immediate summary. Use the Incident Advisor to get a human-readable narrative. Instead of manual data correlation, you can instantly see the "What," "Why," and "How" of the attack.
Action: Click on the incident, review the automated summary in Incident Advisor, and use the Generate Report function to provide an executive-ready PDF report in seconds
How do I find out how the attacker got in and where they went?
Security alerts often show the final malicious payload but not the origin. Use Root Cause Analysis (RCA) to trace the execution chain backward.
Action: Open the RCA graph and follow the critical path. By looking at the process tree, you can identify if the attack started via a spear-phishing email or a compromised service. The Graph view in Extended RCA will show you if the attacker moved from one endpoint to another, for example, using stolen credentials.
How do I stop an active threat on the endpoint and collect evidence?
If you detect a suspicious script running on a server, you need to act without crashing the system.
Action: In the incident Graph section, Isolate the compromised endpoint from the network to block lateral movement attempts. Use the View processes in Live Search option to verify active processes in real-time and identify the specific Process ID (PID) of the threat. Use Remote Connection to open a terminal session and execute the kill command with the identified PID. Finally, go to the Forensics section to create and download an Investigation Package to capture memory dump and logs.
Recommended Content
To learn more about the technologies included in the Detection layer we recommend reading the next article Live Search.
More Resources
Watch our demo to see Incident Advisor in action: YouTube Demo
GravityZone Incident Guided Tour: Incident Guided Tour
Discover the Detection, Response, and Incident Management full potential with our dedicated video masterclasses: Masterclass