Proactive Hardening and Attack Surface Reduction (PHASR) – Bitdefender TechZone
Bitdefender PHASR proactively hardens systems by analyzing user behavior to prevent "Living off the Land" attacks and targeted threats. It uses anomaly detection to enable tailored, application action-level blocking, reducing your attack surface without disrupting operations.
Attackers always favor stealth, leveraging compromised accounts and legitimate tools to blend in and avoid detection. This tactic, known as "Living off the Land" (LOTL), allows them to exploit existing software and user privileges, making their malicious activities appear as normal system operations. Both Bitdefender Labs and our MDR teams have observed this in nearly every major incident.
What drives such a wide range of attackers, from ransomware affiliates to APT groups, to consistently rely on these techniques? Modern cybercriminals have developed standardized playbooks that rely on a combination of stealthy initial access (often gained through compromised credentials or from unmanaged devices) with abuse of existing tools present on virtually every system. These repeatable playbooks allow for efficient, repeatable attacks. Tools like PowerShell or Certutil are deeply embedded in the Windows ecosystem, used not only by administrators but also by many third-party applications, meaning that disabling them would likely cause significant operational disruptions.
Traditional security solutions, with static rules and one-size-fits-all policies, are ill-equipped to handle this new type of attack. This is where PHASR comes in.
Introducing PHASR: Proactive Hardening and Attack Surface Reduction
PHASR is a revolutionary technology that understands that your users are unique and require tailored protection. By analyzing how individuals interact with their systems and applications, PHASR proactively identifies and closes unnecessary attack entry points.
PHASR uses AI-powered analysis to automatically generate unique behavioral profiles for every machine-user combination. For instance, a privileged user will have one profile for their regular workstation activities and another separate profile for their server administration tasks. By grouping individual behavioral profiles based on observed activity, instead of job titles or departments, PHASR enables security teams to apply consistent rules across similar users, reducing management complexity and saving time.
PHASR identifies potential security gaps by comparing consolidated behavioral profiles against common threat actor actions, a library continuously updated with Bitdefender Threat Intelligence (TI) and the expertise of our Labs and MDR teams. Typically, there's no overlap between legitimate user behavior and these threat actor actions. In such cases, PHASR recommends or executes security policy modifications to prevent potential account abuse if a compromise occurs.
PHASR performs granular analysis, comparing 'user actions' to 'attacker tactics'. While process-based rules address clear threats like cryptominers, most detections are context-aware and action-driven. WMIC, for example, is allowed for system information but blocked for lateral movement. This action-level blocking, combined with the layered analysis of user and attacker behavior, enables tailored protection without business disruption.
PHASR: Overview
PHASR learns and adapts to your environment through a 20- 60-day learning phase, depending on the monitored rules. If you are using the EDR component of GravityZone, PHASR can use historical data to shorten the learning phase duration to a few minutes. Following this, PHASR can operate in Autopilot mode, automatically applying security policies, or in Direct Control mode, providing recommendations for manual review. It monitors processes within five defined activity types:
Living Off The Land Binaries – tools, such as PowerShell.exe, WMIC.exe, and Ftp.exe, are pre-installed within an operating system for administrative and operational purposes. Attackers abuse them to perform malicious activities and blend them with normal system activity.
Tampering Tools – tools, such as procexp.exe, vmmap.exe, and LiveKd.exe, are utilities used to modify software applications. They are leveraged for bypassing security controls.
Piracy Tools - software piracy tools such as keygen and crack. They are used to bypass software licensing and activation.
CryptoMiners – tools such as PhoenixMiner, XMRig, and CCMiner, use a computer's processing power to generate cryptocurrency. They are abused for cryptojacking through unauthorized installation on the victim's system.
Remote Admin Tools - often used for legitimate systems management, enable remote access and control of computer systems. Attackers use them to gain unauthorized access and deploy malware.
Each activity type can be independently configured within PHASR. You can choose whether to receive recommendations in Direct control mode, enable automatic management via Autopilot mode, or exclude it from monitoring. Be aware that the PHASR dashboard will not display any recommendations or information for activity types set to Autopilot mode or excluded from monitoring.
Request Access option simplifies the process of allowing end-users to ask for access (and add a business reason note) to an application or command that has been restricted by PHASR in both Autopilot and Direct Control modes. In both modes, the request immediately generates a recommendation to allow access. This recommendation must be reviewed and approved by an administrator. Once approved, PHASR grants the user access to the application or command. The approval simultaneously updates the PHASR monitored rules (for Direct Control mode) or allows the user immediate usage (for Autopilot mode). Even though the application or command was eventually allowed by the administrator, PHASR continues to monitor and learn the application's usage. If a user stops using the application, PHASR will block the application for that user in Autopilot mode based on the learned behavior. In Direct Control mode, this usage change will trigger new rule-optimization recommendations.
PHASR Dashboard is available in GravityZone Platform under the Monitoring -> ASM dashboard in the PHASR section and allows you to pivot and view detailed information in widgets about:
Attack surface exposure – this shows your company's current attack surface exposure, indicating the percentage of potentially exploitable attack vectors. The lower the level, the more potential entry points have been blocked.
Top recommendations by impact - this shows the top recommendations to reduce the attack surface.
Detected incidents for monitored attack vector categories - it shows if there are any incidents that triggered rules from a monitored category. Selecting an incidents will direct you to the Incident section in GravityZone.
Living of the land binaries, Tampering and Hack tools, Miners, and Remote admin tools – it shows the number of behavioral profiles with and without their usage, and the top four recommendations to maximize attack surface reduction.
PHASR's Recommendation page offers a detailed view of potential actions to reduce your attack surface. This comprehensive list includes information for each recommendation, such as its attack surface reduction score, targeted activity type, monitored rules, behavioral profiles, and actions already taken.
When PHASR operates in Direct Control mode, these recommendations become crucial to your internal risk management process. In this mode, you can define whether to allow or restrict a specific action. PHASR will then guide you through the process of changing which users and devices are affected by that recommendation, all based on their assigned behavioral profiles
These recommendations are not static; they are dynamically generated by PHASR, which continuously monitors user behavior. Recommendations are generated for identified behavioral profiles. A recommendation might encompass multiple behavioral profiles that indicate similar patterns or security gaps. PHASR primarily generates "Restrict access" recommendations for behavioral profiles that, based on their learned activity patterns, are not actively using tools/actions from the monitored categories (e.g., LOTL binaries, tampering tools). If a user's behavior changes over time and they begin to use previously restricted applications or actions, PHASR will adapt by generating "Allow access" recommendations.
You can fine-tune PHASR monitored rules (480+ rules) used in Direct control mode directly from GravityZone within the PHASR monitored rules section, or by clicking on the rule name in the PHASR recommendations section. Each rule includes information about recommendations (restrict or allow access), targeted activity type, behavioral profiles (all profiles grouped for the rule), restricted behavioral profiles (profiles where the rule was applied), and action.
Visualizing PHASR: Direct Control vs. Autopilot
To further illustrate the operational flexibility of PHASR, the following diagrams present its workflow in both Direct Control and Autopilot modes.
PHASR in Direct Control mode
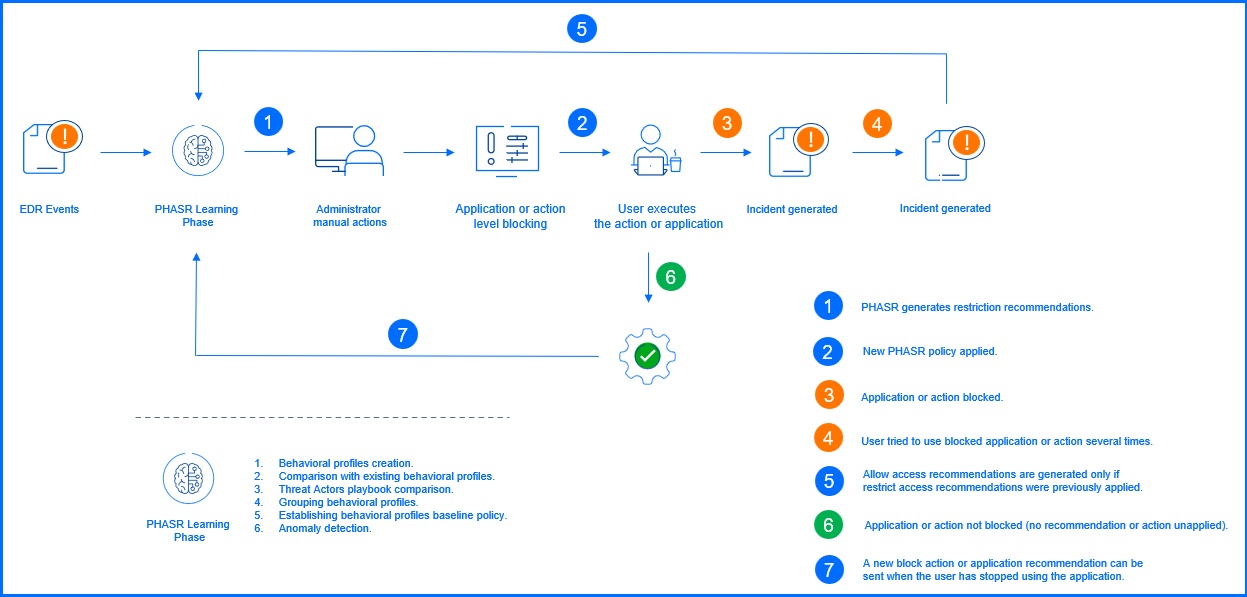
In Direct Control mode, PHASR acts as an intelligent advisor. After its initial learning phase, it continuously analyzes user behavior to identify potential attack surface reduction opportunities. These recommendations are then presented to your security team for review and manual approval.
PHASR in Autopilot mode
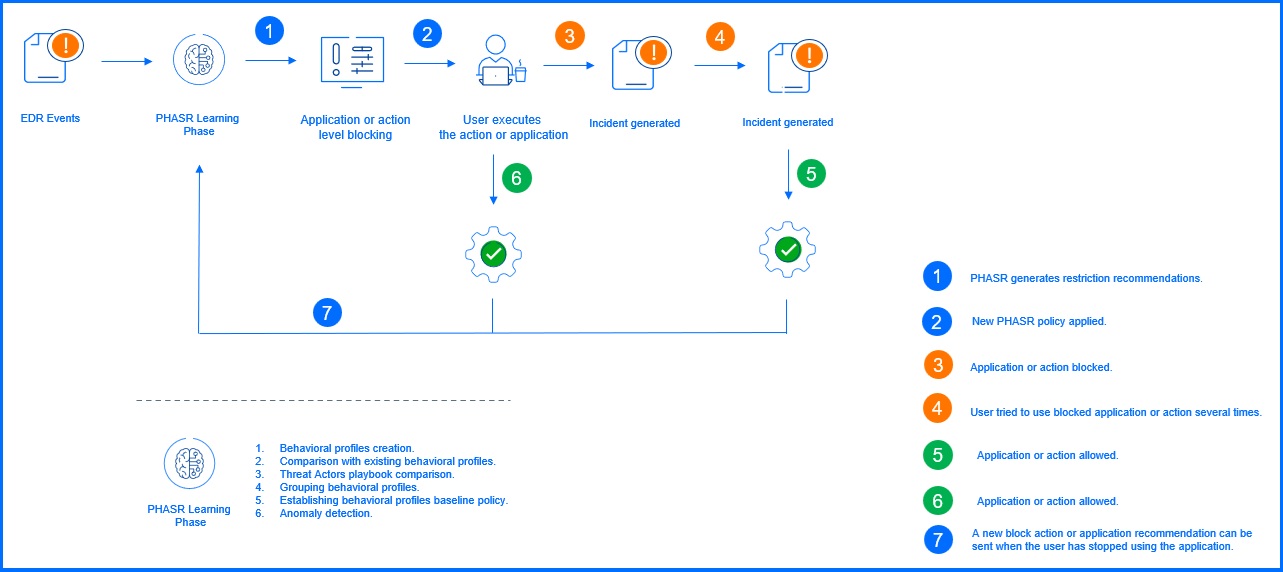
Autopilot mode represents the automated attack surface reduction with PHASR. Once the learning phase is complete, PHASR takes the initiative to automatically apply security policy modifications based on its continuous analysis of behavioral. In this mode, PHASR proactively hardens your environment without requiring manual intervention for each recommendation.
PHASR: A Unique Approach to Security
Unlike traditional methods that rely on static policies, PHASR dynamically adapts to user behavior. It provides tailored recommendations, enabling security teams to implement the most effective policies. Through continuous analysis of user and application behavior, this approach extends to action-level blocking, allowing for selective restriction of high-risk actions rather than entire applications. PHASR makes it easy to identify and block attacks that deviate from normal activity.
Precise: Unlike one-size-fits-all security solutions, PHASR enables precise and proactive tailoring of hardening settings based on individual behavior. Instead of allowing or restricting entire applications, PHASR enables action-level blocking, selectively restricting high-risk actions that deviate from typical user behavior.
Adaptive: PHASR operates on a continuous learning cycle. It continuously analyzes user actions, adapting to new behaviors, while our research teams simultaneously update its rules based on the most recent threat actor playbooks.
Frictionless: PHASR seamlessly integrates with your existing security infrastructure and requires minimal intervention from your security team. By reducing your attack surface without business disruptions, PHASR allows your security team to focus on other critical threats.
PHASR Standalone Deployment
To ensure maximum operational flexibility, PHASR is not limited to integrated deployment within the full GravityZone security stack. You can now integrate PHASR as a standalone agent into your existing Windows endpoint security architecture. This option provides full access to all of PHASR’s core functionalities, including:
Viewing and fine-tuning PHASR-monitored rules.
Receiving tailored recommendations for reducing the attack surface.
Applying "Restrict access" and "Allow access" recommendations.
All management, monitoring, and policy modifications for the standalone agent are available directly in the GravityZone console or through the API. It is important to note that when using this standalone installation package, the learning period cannot be accelerated using historical data from an EDR module.
This flexibility allows you to deploy PHASR’s unique hardening and attack surface reduction capabilities in any environment, even those where other security solutions are already installed.
PHASR in Action: An Example
Imagine an employee who needs temporary access to PowerShell for a specific task. An administrator grants this access but forgets to revoke it later. PHASR would detect the user's lack of PowerShell activity and recommend revoking access, preemptively eliminating a potential attack vector.
When directly blocking PowerShell is not an option, PHASR provides granular security through action-level blocking. This allows legitimate PowerShell usage while preventing malicious actions. For instance, even if a user frequently uses PowerShell, PHASR will block only high-risk commands like obfuscated or encrypted scripts, which are typically associated with threat actors.
More Resources
Bitdefender PHASR official website: Bitdefender PHASR
Discover the full potential with our dedicated video masterclasses: Bitdefender Masterclass
Bitdefender PHASR deployment and monitoring guide: PHASR Guided Tour
Bitdefender PHASR product overview: PHASR product overview
To request a demo or learn more information, click here.
Recommended Content
To learn more about the technologies included in the Prevention layer, we recommend reading the next article External Attack Surface Management (EASM).