YARA Rules - Bitdefender TechZone
Learn how to use YARA rules in Bitdefender GravityZone and create custom detection patterns with automatic response actions for Zero-Day threats and specific TTPs, enhancing threat hunting capabilities across Windows, macOS, and Linux.
To provide an additional layer of network protection against advanced threats, consider using detection data based on real-world attack patterns specific to your country or industry. You can approach this in two ways. Firstly, you can use Indicators of Compromise (IoCs), which are digital artifacts or forensic clues discovered during the investigation of a security incident. However, attackers can simply recompile the file and rotate their network, limiting the long-term effectiveness of IoCs. Therefore, you can move beyond simple IoC matching and use the capability to recognize and block unique Tactics, Techniques, and Procedures (TTPs).
This is where YARA rules in the GravityZone platform are critical, as they empower your security team to create finely tuned organization-specific detection patterns that identify and classify malware families or threat actors.
YARA Rules
YARA stands for Yet Another Recursive Acronym and was developed by Victor Alvarez. YARA rules are a customizable pattern-matching mechanism used for identifying and classifying data or files based on specified conditions. These conditions are written in a specialized YARA rule language, allowing for precise and customizable detection rules. When a system scans files or data, it checks them against these rules to identify matches, triggering specific actions or alerts when a match is found.
YARA rules can be valuable assets for:
Zero-day Detection: Creating rules to detect vulnerable software that was not patched by the manufacturer or malware attempting to exploit it.
Threat Hunting: Proactively hunting for specific patterns and IoCs to identify threats that may have gone undetected by traditional security tools.
Custom Security Policy: Enforcing specific policies, such as blocking files with defined characteristics.
Forensic and Incident Response: Identifying files/artifacts associated with known threats to scope and stop security incidents.
YARA Rule Deployment
You can create your custom rules or acquire pre-existing ones from various publicly accessible repositories. The YARA community is a highly active ecosystem, constantly contributing new detection patterns and sharing resources through repositories. Security experts and professionals frequently distribute YARA rules for recently identified threats on social media platforms such as Twitter or Reddit. Additionally, these YARA rules can be freely accessed and downloaded from repositories like GitHub or specialized vendors, some of whom may provide their YARA rules as part of paid subscription services.
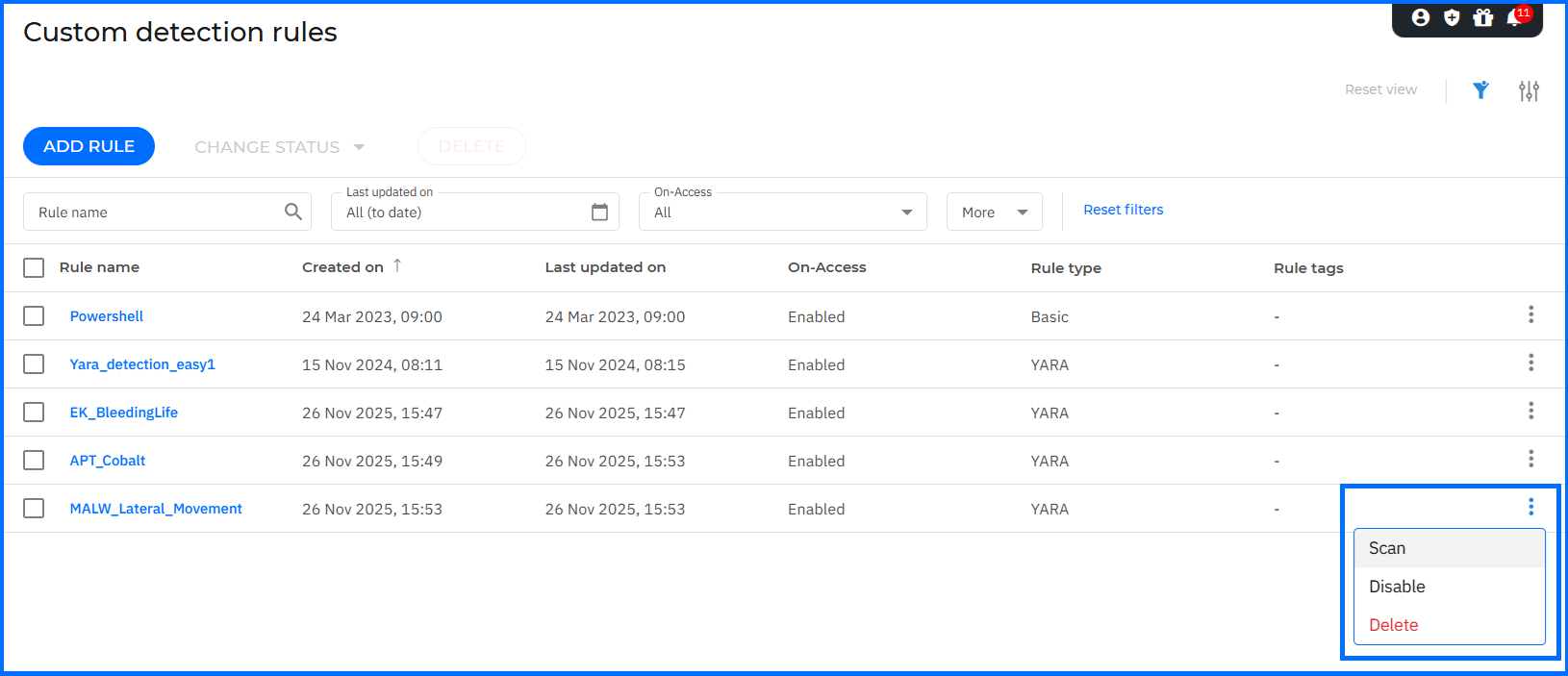
With Bitdefender GravityZone, you receive YARA available for Microsoft, macOS, and Linux operating systems under an EDR subscription. The configuration is available directly in GravityZone under Custom detection rules. The YARA rule operates in two modes:
On-access: Generates incidents and alerts based on rules that match the configured file pattern. For example, if a YARA rule is designed to detect a specific malware signature within files, on-access scanning would trigger an alert or take action whenever a file with the matching signature is accessed or executed in real-time.
On-Demand: This is a manual scan of the entire disk or specific folders, typically used for proactive threat hunting or post-incident verification. You can execute it within GravityZone by navigating to Custom detection rules, selecting the desired YARA rule, and using the Scan command.
 |
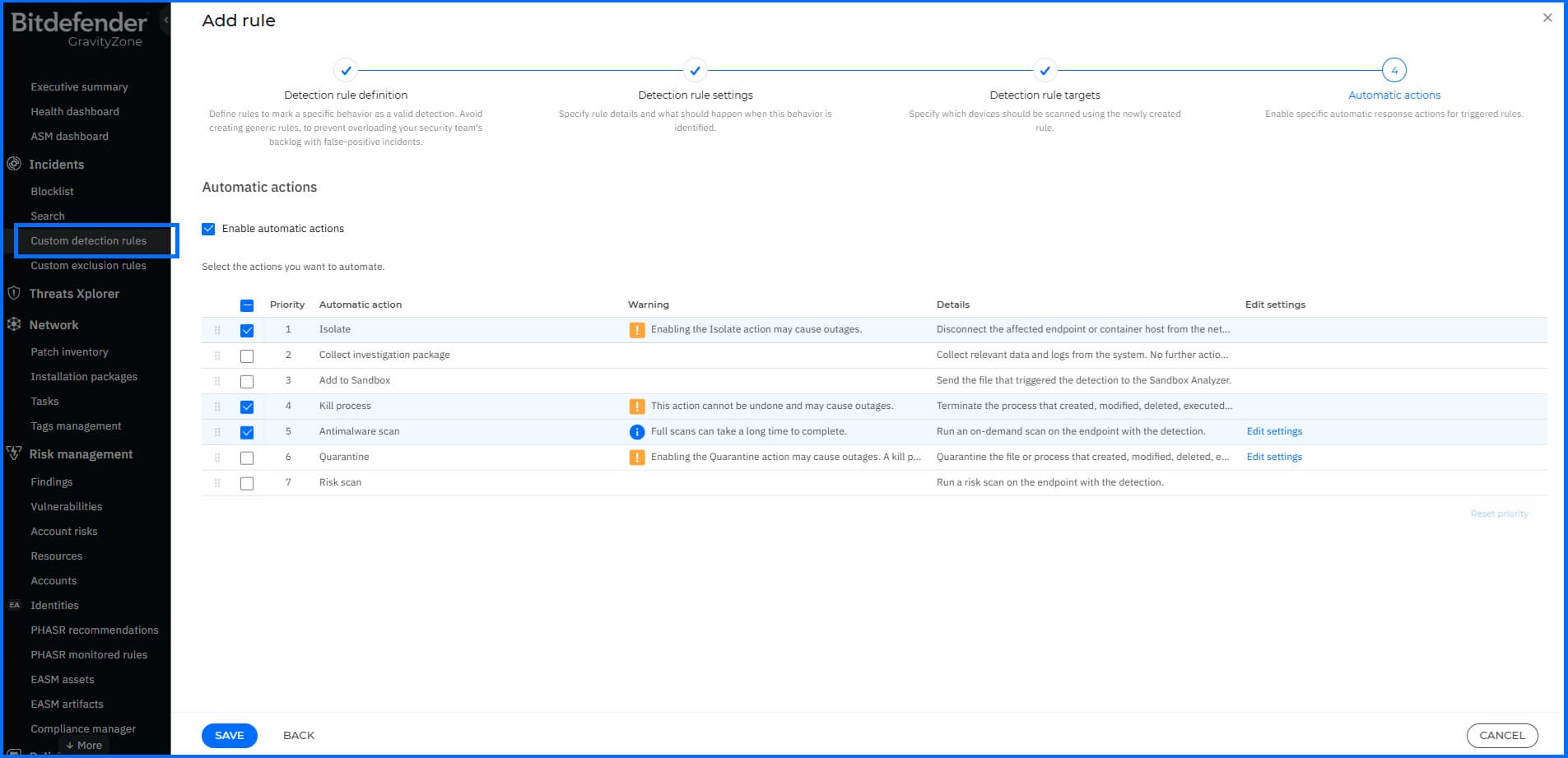
Yara Rules Actions
You can define an automatic action that will be executed when YARA rules match the search:
Isolate endpoint.
Kill process.
Quarantine.
Add to Sandbox.
Antimalware scan.
Risk scan.
Collect investigation package.
 |
Detailed YARA configuration instructions can be found in the GravityZone Support Center here.
Detection Visualization
You can monitor YARA-based detections across GravityZone: on-access scans automatically generate entries in the Incidents section for deep analysis, while results from on-demand scans are available as alerts in the Search > Historical section.
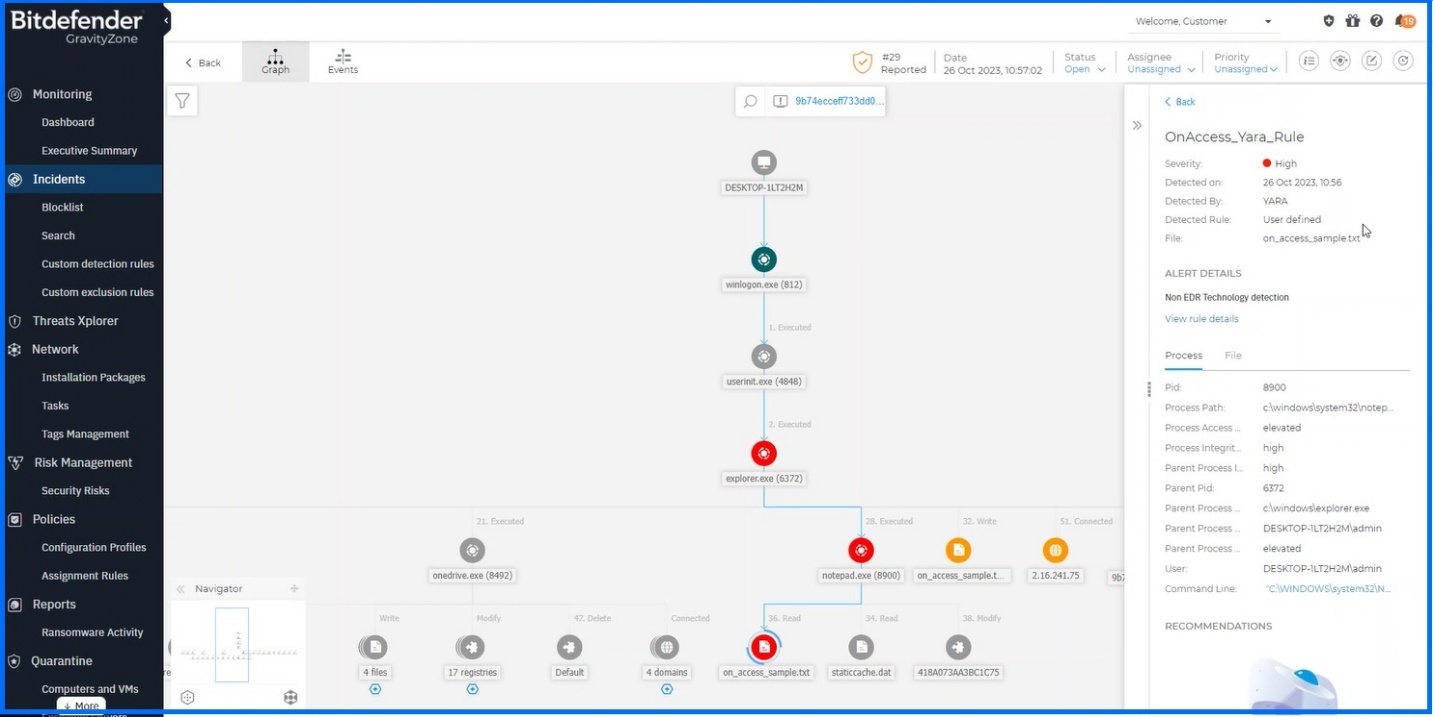 YARA, on-access scan results. | ||
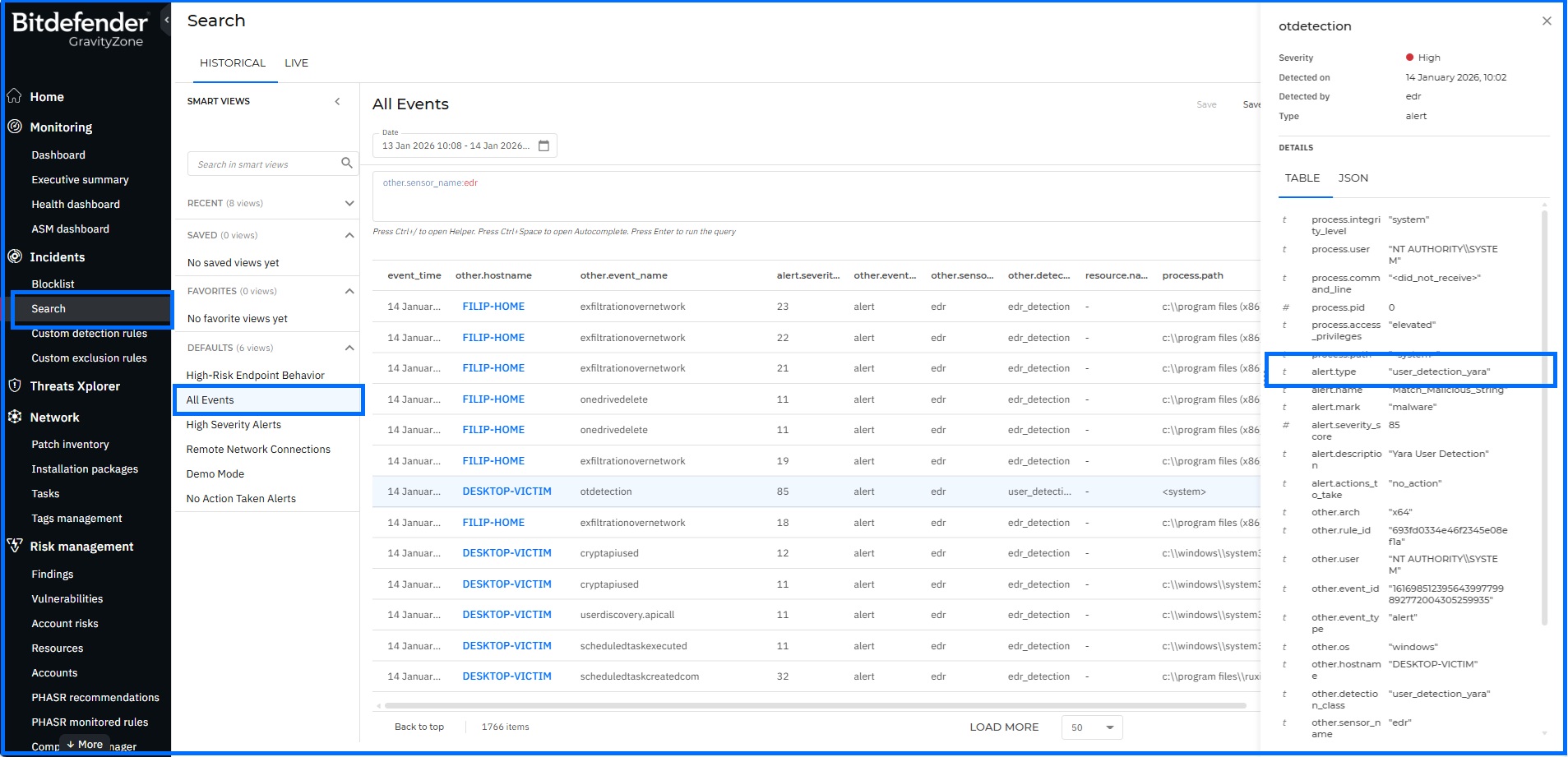 YARA, on-demand scan results. |
YARA Rules in Action: An Example
Recommended Content
To learn more about the technologies included in the Detection layer we recommend reading the next article Anomaly Detection.